- 888
- 245
The US Department of State has announced a reward of up to $10 million for information on hackers working for foreign governments and associated with the RedLine malware, as well as on the alleged creator of this malware, Maxim Rudometov. The reward also covers information on the use of RedLine in cyberattacks against critical infrastructure facilities in the United States.
The Rewards for Justice program specifically notes that the information must concern cyberattacks carried out at the direction or under the control of foreign governments and violating the provisions of the US Computer Fraud and Abuse Act. In particular, of interest are participants in cyber operations involving the RedLine malware, a popular infostealer used to steal user credentials.
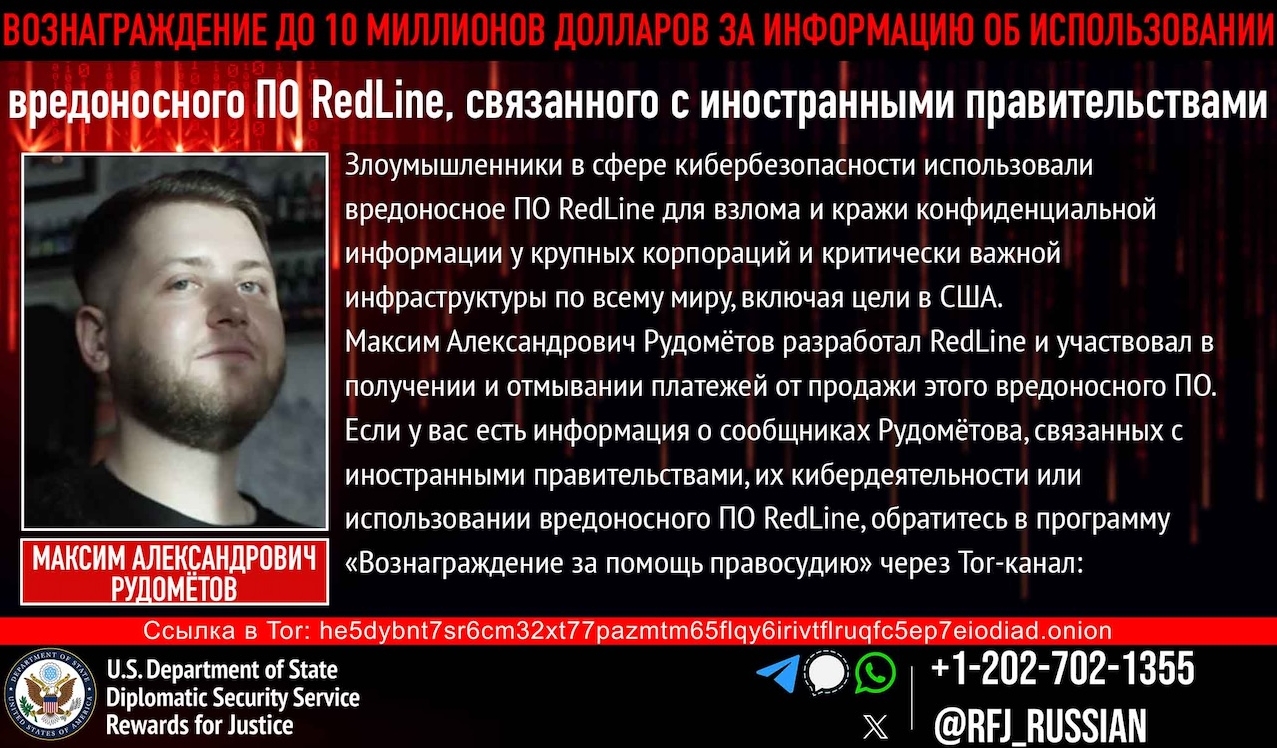
[td]State Department Rewards for Justice poster[/td]The State Department noted that anyone with information about Rudometov’s accomplices or their malicious cyber activities or the use of RedLine malware should contact Rewards for Justice via a Tor-based messaging channel .
U.S. authorities believe that Maxim Rudometov was the developer and administrator of the entire RedLine Infostealer infrastructure. In October 2024, charges were brought against him as part of the international Operation Magnus , during which U.S. law enforcement agencies and their international partners conducted a large-scale operation to suppress the activities of two services at once - RedLine and META , which operated on the malware-as-a-service (MaaS) model.
According to the U.S. Department of Justice, Rudometov managed RedLine servers, received and laundered proceeds through cryptocurrency wallets, and directly interacted with the code and distribution of malware. During the investigation, his connections to key distribution channels were established, including Telegram accounts used to promote and sell malware to end users. To date, more than 1,200 servers used to control the RedLine and META botnets have been discovered.
The Dutch police and the Eurojust agency also participated in the operation. Two suspects were arrested in Belgium, three servers and two domains used as control nodes were seized. However, it has not been officially confirmed whether Rudometov himself was detained. If found guilty, he could face up to 35 years in prison on charges of access device fraud, conspiracy to commit computer intrusion, and money laundering.
The Rewards for Justice program specifically notes that the information must concern cyberattacks carried out at the direction or under the control of foreign governments and violating the provisions of the US Computer Fraud and Abuse Act. In particular, of interest are participants in cyber operations involving the RedLine malware, a popular infostealer used to steal user credentials.

U.S. authorities believe that Maxim Rudometov was the developer and administrator of the entire RedLine Infostealer infrastructure. In October 2024, charges were brought against him as part of the international Operation Magnus , during which U.S. law enforcement agencies and their international partners conducted a large-scale operation to suppress the activities of two services at once - RedLine and META , which operated on the malware-as-a-service (MaaS) model.
According to the U.S. Department of Justice, Rudometov managed RedLine servers, received and laundered proceeds through cryptocurrency wallets, and directly interacted with the code and distribution of malware. During the investigation, his connections to key distribution channels were established, including Telegram accounts used to promote and sell malware to end users. To date, more than 1,200 servers used to control the RedLine and META botnets have been discovered.
The Dutch police and the Eurojust agency also participated in the operation. Two suspects were arrested in Belgium, three servers and two domains used as control nodes were seized. However, it has not been officially confirmed whether Rudometov himself was detained. If found guilty, he could face up to 35 years in prison on charges of access device fraud, conspiracy to commit computer intrusion, and money laundering.
