- 883
- 242
How Trojans Take Control of a Smartphone Through a Dialog Box.
Researchers at CYFIRMA have warned of a new wave of attacks using malicious Android apps that disguise themselves as legitimate banking clients to steal user data, intercept messages, and conduct unauthorized financial transactions. According to analysts, these programs are particularly active in targeting Indian bank clients and use advanced methods of disguise and bypassing protection. The main malware is distributed through fake websites, instant messengers, phishing messages, and even fake system updates.
Once installed, the app requests critical permissions and launches hidden activity without the user noticing. The malware can read and send SMS, intercept one-time codes and notifications, track phone calls, and collect SIM card data. It uses Firebase as a channel for managing and storing stolen information, and also uses auto-start methods when the device is rebooted to maintain its presence.
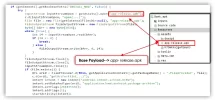
One of the features of the attack is its modular architecture. The malware consists of two parts: a dropper and the main payload. First, an APK dropper is downloaded, which uses a hidden installation mechanism and imitates the actions of a regular application. After that, using a specially configured interface, the user is tricked into installing a second APK file, which contains data theft functions. The main component is hidden from the list of applications, does not show an icon, and works completely in the background.
Social engineering mechanisms play a key role. The user is shown fake input forms that completely imitate the interface of a real banking application. Even the length of the phone number and PIN code is checked, which enhances the feeling of authenticity. The collected data, including CVV, card numbers, MPIN and one-time codes, are sent to the Firebase cloud database. From there, attackers gain access to confidential information and can control infected devices.
Analysis also showed that the malware is capable of executing remote commands via push notifications, automatically enabling call forwarding, performing USSD requests and using system permissions to collect metadata. Using Firebase makes the command and control infrastructure invisible, as the service is free and does not require authentication by default.
Such applications are distributed through many channels. Among them are fake bank websites, SEO manipulations, infected third-party app stores, malicious QR codes and NFC tags. Sometimes such applications are disguised as system utilities, for example, Play Protect updates or battery managers. In some cases, the malware can be pre-installed on cheap devices or distributed via USB with physical access to the phone.
CYFIRMA experts urge users to disable the ability to install applications from unknown sources and not to follow suspicious links in SMS and instant messengers. They also recommend using EDR class solutions for mobile devices that are able to track the behavior of applications in real time. For banks and telecom companies, integration with threat-oriented traffic filtering systems and active monitoring of abuse of cloud platforms is offered.
According to experts, this campaign demonstrates the high level of training of attackers and the vulnerability of the Android ecosystem in the absence of centralized control. The slightest carelessness on the part of the user can lead to a complete compromise of their financial data.
Researchers at CYFIRMA have warned of a new wave of attacks using malicious Android apps that disguise themselves as legitimate banking clients to steal user data, intercept messages, and conduct unauthorized financial transactions. According to analysts, these programs are particularly active in targeting Indian bank clients and use advanced methods of disguise and bypassing protection. The main malware is distributed through fake websites, instant messengers, phishing messages, and even fake system updates.
Once installed, the app requests critical permissions and launches hidden activity without the user noticing. The malware can read and send SMS, intercept one-time codes and notifications, track phone calls, and collect SIM card data. It uses Firebase as a channel for managing and storing stolen information, and also uses auto-start methods when the device is rebooted to maintain its presence.

One of the features of the attack is its modular architecture. The malware consists of two parts: a dropper and the main payload. First, an APK dropper is downloaded, which uses a hidden installation mechanism and imitates the actions of a regular application. After that, using a specially configured interface, the user is tricked into installing a second APK file, which contains data theft functions. The main component is hidden from the list of applications, does not show an icon, and works completely in the background.
Social engineering mechanisms play a key role. The user is shown fake input forms that completely imitate the interface of a real banking application. Even the length of the phone number and PIN code is checked, which enhances the feeling of authenticity. The collected data, including CVV, card numbers, MPIN and one-time codes, are sent to the Firebase cloud database. From there, attackers gain access to confidential information and can control infected devices.
Analysis also showed that the malware is capable of executing remote commands via push notifications, automatically enabling call forwarding, performing USSD requests and using system permissions to collect metadata. Using Firebase makes the command and control infrastructure invisible, as the service is free and does not require authentication by default.
Such applications are distributed through many channels. Among them are fake bank websites, SEO manipulations, infected third-party app stores, malicious QR codes and NFC tags. Sometimes such applications are disguised as system utilities, for example, Play Protect updates or battery managers. In some cases, the malware can be pre-installed on cheap devices or distributed via USB with physical access to the phone.
CYFIRMA experts urge users to disable the ability to install applications from unknown sources and not to follow suspicious links in SMS and instant messengers. They also recommend using EDR class solutions for mobile devices that are able to track the behavior of applications in real time. For banks and telecom companies, integration with threat-oriented traffic filtering systems and active monitoring of abuse of cloud platforms is offered.
According to experts, this campaign demonstrates the high level of training of attackers and the vulnerability of the Android ecosystem in the absence of centralized control. The slightest carelessness on the part of the user can lead to a complete compromise of their financial data.
