- 3,015
- 282
- 1,730
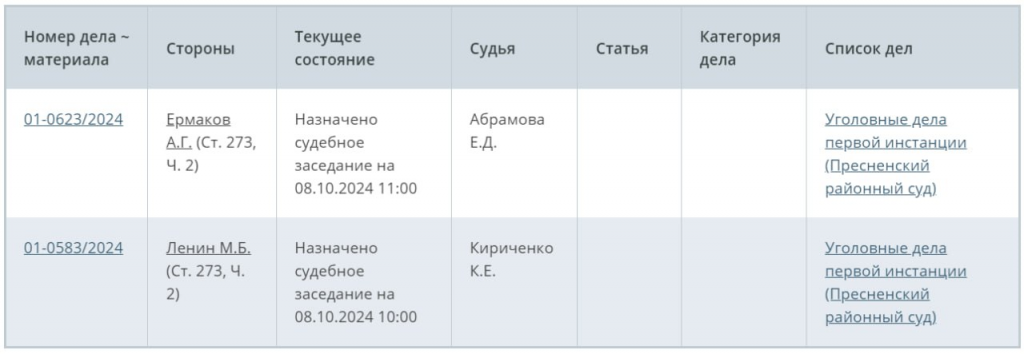
On October 8, the Presnensky District Court of Moscow has scheduled hearings on the cases of Ermakov A.G. and Lenin M.B. Both defendants are charged under Article 273, Part 2 of the Criminal Code of the Russian Federation — creation, use or distribution of malicious computer programs committed by a group of persons or an organized group, or causing major damage or committed out of selfish interest.
Most likely, the defendants are Ermakov Aleksandr Gennadyevich and Lenin (Shefel) Mikhail Borisovich. It is assumed that this case is related to the activities of the extortion group known as SugarLocker. Earlier in February, Russian law enforcement agencies, together with the FACCT company, arrested members of the SugarLocker cybercriminal group, disguised as the legitimate IT company Shtazi-IT. The group offered services for the development of landing pages, mobile applications and online stores, using these platforms to distribute malware. The investigation revealed that the SugarLocker ransomware (Encoded01) was created in early 2021, but was not actively used initially. In November of that year, a user under the pseudonym "GustaveDore" on the underground RAMP forum introduced a Ransomware-as-a-Service (RaaS) affiliate program, soliciting partnerships to use the SugarLocker ransomware. The ad stated that the group infiltrates victims' networks via RDP (Remote Desktop Protocol) and offers partners 70% of the revenue, leaving 30% for SugarLocker. For revenues above $5 million, the profit split changes to 90% in favor of the partner and 10% for SugarLocker. In January 2024, three members of the group, including Alexander Ermakov (known under the pseudonyms blade_runner and GustaveDore), were arrested. The investigation found that Ermakov was involved in the attacks on Medibank Private, which resulted in the leak of data of 10 million Australians. @ SecurityLab
Most likely, the defendants are Ermakov Aleksandr Gennadyevich and Lenin (Shefel) Mikhail Borisovich. It is assumed that this case is related to the activities of the extortion group known as SugarLocker. Earlier in February, Russian law enforcement agencies, together with the FACCT company, arrested members of the SugarLocker cybercriminal group, disguised as the legitimate IT company Shtazi-IT. The group offered services for the development of landing pages, mobile applications and online stores, using these platforms to distribute malware. The investigation revealed that the SugarLocker ransomware (Encoded01) was created in early 2021, but was not actively used initially. In November of that year, a user under the pseudonym "GustaveDore" on the underground RAMP forum introduced a Ransomware-as-a-Service (RaaS) affiliate program, soliciting partnerships to use the SugarLocker ransomware. The ad stated that the group infiltrates victims' networks via RDP (Remote Desktop Protocol) and offers partners 70% of the revenue, leaving 30% for SugarLocker. For revenues above $5 million, the profit split changes to 90% in favor of the partner and 10% for SugarLocker. In January 2024, three members of the group, including Alexander Ermakov (known under the pseudonyms blade_runner and GustaveDore), were arrested. The investigation found that Ermakov was involved in the attacks on Medibank Private, which resulted in the leak of data of 10 million Australians. @ SecurityLab

