- 888
- 245
The RedCurl group, which usually specializes in covert corporate espionage, has started using QWCrypt ransomware designed to attack Hyper-V virtual machines.
The Russian-language RedCurl hacking group was first discovered by Group-IB specialists in 2020 . The researchers wrote that the group has been active since at least 2018, and even then the attackers carried out a number of targeted attacks on commercial organizations, including construction, financial, consulting companies, as well as retailers, banks, insurance, legal and tourism organizations.
The group's victims were located in Russia, Ukraine, Great Britain, Germany, Canada and Norway, but last year it became known that RedCurl had expanded the geography of its attacks, attacking targets in Southeast Asia and Australia. As Bitdefender
researchers now warn , the group has changed tactics and begun deploying ransomware on the networks of its victims.
[td]"In most cases, we observed that RedCurl followed its usual pattern and continued to steal data over long periods of time. But one case stood out. The hackers broke their usual pattern and used ransomware for the first time," the experts say.[/td]As enterprises increasingly use virtual machines to host their servers, ransomware groups are following the trend and creating ransomware that specifically targets virtualization platforms. But while most ransomware operations target VMware ESXi servers, the new QWCrypt ransomware, which uses RedCurl, targets Hyper-V virtual machines.
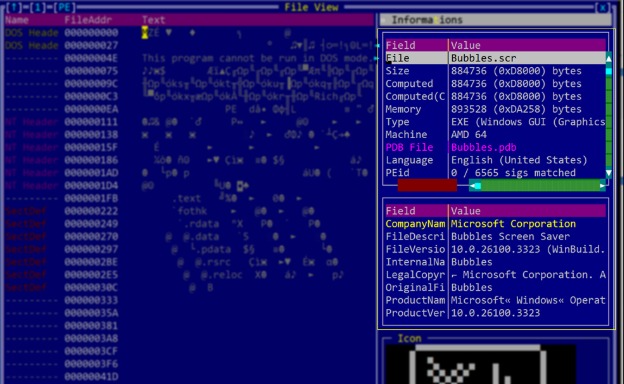
The attacks discovered by Bitdefender begin with phishing emails with .IMG attachments disguised as resumes. IMG files are disk images that are automatically mounted by Windows under a new drive letter when double-clicked.
These files contain a screensaver that is vulnerable to DLL sideloading using a legitimate Adobe executable, which downloads the payload and persists on the system via a scheduled task.
RedCurl uses a living-off-the-land tactic to hide in compromised Windows systems, as well as its own wmiexec variant for lateral movement across the network and the Chisel tool for tunneling/RDP access.
To disable security measures before deploying the ransomware, the attackers use encrypted 7z archives and a multi-step PowerShell process.
Unlike Windows ransomware, QWCrypt supports numerous command-line arguments that are used to customize the attacks. For example, in the attacks analyzed by Bitdefender, RedCurl used the --excludeVM argument to not encrypt virtual machines that acted as network gateways to avoid failures.
When encrypting files, QWCrypt (rbcw.exe) uses the XChaCha20-Poly1305 encryption algorithm and appends the .locked$ or .randombits$ extension to the encrypted files.
It is noted that the ransomware can use intermittent or selective encryption of files depending on their size to increase the speed of operation.
Since RedCurl does not have a separate website for "draining" stolen data and double extortion, it is not entirely clear whether the ransomware is used as a false flag, or the group has actually decided to engage in extortion.
Researchers believe that RedCurl is a group of mercenaries who offer their services to third parties, which can lead to a mixture of espionage and financially motivated attacks. Also, ransomware can be a diversionary maneuver covering up the theft of data, or a backup way to monetize access if the client has not paid for the main services (data collection).
Another theory of the researchers is that RedCurl may indeed be engaged in extortion for financial gain, but prefers to act quietly, arranging closed negotiations and not publishing its demands or the data stolen from victims.
The Russian-language RedCurl hacking group was first discovered by Group-IB specialists in 2020 . The researchers wrote that the group has been active since at least 2018, and even then the attackers carried out a number of targeted attacks on commercial organizations, including construction, financial, consulting companies, as well as retailers, banks, insurance, legal and tourism organizations.
The group's victims were located in Russia, Ukraine, Great Britain, Germany, Canada and Norway, but last year it became known that RedCurl had expanded the geography of its attacks, attacking targets in Southeast Asia and Australia. As Bitdefender
researchers now warn , the group has changed tactics and begun deploying ransomware on the networks of its victims.
The attacks discovered by Bitdefender begin with phishing emails with .IMG attachments disguised as resumes. IMG files are disk images that are automatically mounted by Windows under a new drive letter when double-clicked.
These files contain a screensaver that is vulnerable to DLL sideloading using a legitimate Adobe executable, which downloads the payload and persists on the system via a scheduled task.

RedCurl uses a living-off-the-land tactic to hide in compromised Windows systems, as well as its own wmiexec variant for lateral movement across the network and the Chisel tool for tunneling/RDP access.
To disable security measures before deploying the ransomware, the attackers use encrypted 7z archives and a multi-step PowerShell process.
Unlike Windows ransomware, QWCrypt supports numerous command-line arguments that are used to customize the attacks. For example, in the attacks analyzed by Bitdefender, RedCurl used the --excludeVM argument to not encrypt virtual machines that acted as network gateways to avoid failures.
When encrypting files, QWCrypt (rbcw.exe) uses the XChaCha20-Poly1305 encryption algorithm and appends the .locked$ or .randombits$ extension to the encrypted files.
It is noted that the ransomware can use intermittent or selective encryption of files depending on their size to increase the speed of operation.
Since RedCurl does not have a separate website for "draining" stolen data and double extortion, it is not entirely clear whether the ransomware is used as a false flag, or the group has actually decided to engage in extortion.
Researchers believe that RedCurl is a group of mercenaries who offer their services to third parties, which can lead to a mixture of espionage and financially motivated attacks. Also, ransomware can be a diversionary maneuver covering up the theft of data, or a backup way to monetize access if the client has not paid for the main services (data collection).
Another theory of the researchers is that RedCurl may indeed be engaged in extortion for financial gain, but prefers to act quietly, arranging closed negotiations and not publishing its demands or the data stolen from victims.
