- 888
- 245
The Elusive Comet group is using a little-known feature called Remote Control in Zoom to take control of a victim’s computer, install malware, and steal cryptocurrency.
The issue was discovered by researchers from the nonprofit Security Alliance (SEAL) and Trail of Bits. According to the researchers, North Korean hackers are posing as venture capitalists to send victims phishing emails with links to Zoom meetings.
The attack begins with a standard press release or private message inviting the victim to appear on an Aureon Capital podcast, with the hackers posing as podcast hosts, journalists, and venture capital firms.
If the victim falls for the podcast trick, the hackers set up a Zoom meeting, ostensibly to learn more about the potential victim’s work. Sometimes, the details of the meeting are kept secret until the last minute to create a sense of urgency.
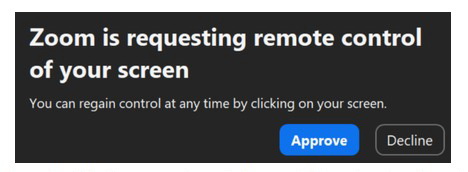
[td]“Once the potential victim joins the conversation, they are asked to share their screen, ostensibly to demonstrate their work. At this point, the hackers use Zoom to request remote control of the victim’s computer. If the potential victim is not paying close attention, they may inadvertently grant the attackers remote access, allowing Elusive Comet to deploy its malware,” the SEAL alert states.[/td]The Remote Control feature allows one user to take control of another meeting participant’s computer if that participant has given explicit permission to do so.
The trick is for one of the hacker group members to join the meeting as Zoom and request remote control of the victim’s system. Since the participant in the video conference is named Zoom, the pop-up looks like a system request for permission from the program itself, which can fool unwary victims.
According to the researchers, the Elusive Comet malware can act as either an infostealer that steals data immediately, or as a RAT (remote access trojan) that allows secrets to be stolen later. Typically, after installation, the malware will start monitoring the victim’s browser sessions, password managers, and look for seed phrases.
SEAL researchers say such attacks have already resulted in “millions in losses,” and their report lists about thirty social media accounts and several corporate websites that were used to give the fake Aureon Capital the appearance of legitimacy.
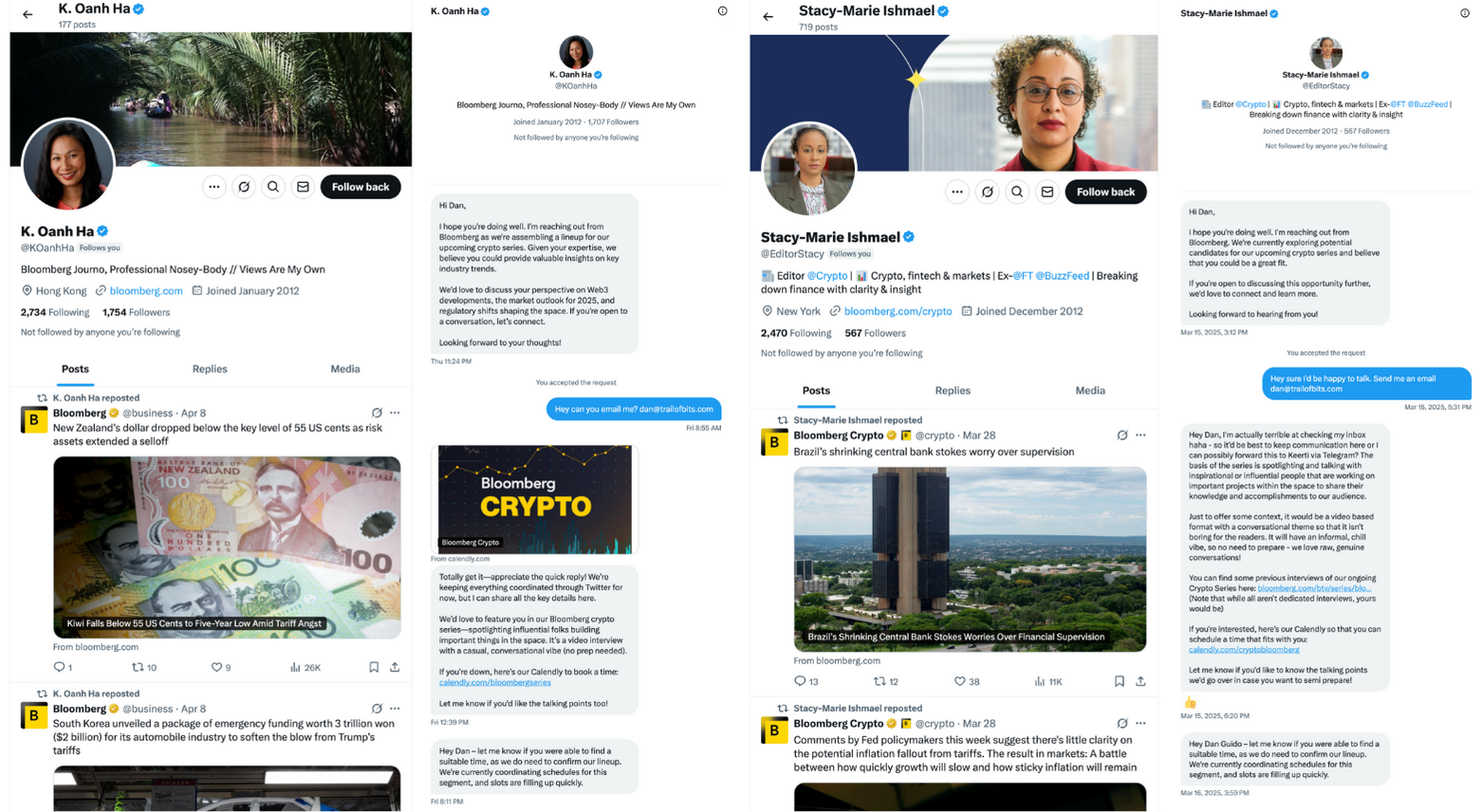
At the same time, experts at Trail of Bits reported that they encountered such attacks personally: two X users posing as Bloomberg producers tried to invite the company's CEO to participate in a Crypto column. The attackers persistently asked the expert to call via Zoom and tried to take control of his machine in the manner described above.
[td]Elusive Comet Fake Profiles[/td]It’s worth noting that Zoom ’s documentation clearly states that Remote Control was never intended to be admin-friendly. This in-meeting option can be disabled by the host, at the account, group, or user level. Administrators can also block Remote Control and the clipboard sharing option, which attackers use to transfer private keys between machines.
However, in practice, few people know about Remote Control at all, and the dialog box looks like a regular Zoom request. Trail of Bits experts argue that it’s this ambiguity in the interface that poses the main danger.
[td]“This attack is especially dangerous because the permission dialog is similar to other harmless notifications from Zoom. Users who are accustomed to clicking “Approve” on Zoom requests may grant complete control of their computer without realizing the consequences,” Trail of Bits warns.[/td]Trail of Bits and Security Alliance experts recommend disabling the remote control feature and the entire Zoom accessibility suite if not in use.
The issue was discovered by researchers from the nonprofit Security Alliance (SEAL) and Trail of Bits. According to the researchers, North Korean hackers are posing as venture capitalists to send victims phishing emails with links to Zoom meetings.
The attack begins with a standard press release or private message inviting the victim to appear on an Aureon Capital podcast, with the hackers posing as podcast hosts, journalists, and venture capital firms.
If the victim falls for the podcast trick, the hackers set up a Zoom meeting, ostensibly to learn more about the potential victim’s work. Sometimes, the details of the meeting are kept secret until the last minute to create a sense of urgency.
The trick is for one of the hacker group members to join the meeting as Zoom and request remote control of the victim’s system. Since the participant in the video conference is named Zoom, the pop-up looks like a system request for permission from the program itself, which can fool unwary victims.

According to the researchers, the Elusive Comet malware can act as either an infostealer that steals data immediately, or as a RAT (remote access trojan) that allows secrets to be stolen later. Typically, after installation, the malware will start monitoring the victim’s browser sessions, password managers, and look for seed phrases.
SEAL researchers say such attacks have already resulted in “millions in losses,” and their report lists about thirty social media accounts and several corporate websites that were used to give the fake Aureon Capital the appearance of legitimacy.
At the same time, experts at Trail of Bits reported that they encountered such attacks personally: two X users posing as Bloomberg producers tried to invite the company's CEO to participate in a Crypto column. The attackers persistently asked the expert to call via Zoom and tried to take control of his machine in the manner described above.

However, in practice, few people know about Remote Control at all, and the dialog box looks like a regular Zoom request. Trail of Bits experts argue that it’s this ambiguity in the interface that poses the main danger.
