- 883
- 242
In late September 2025, Neon, an app that paid users to record their phone calls and sold the data to AI companies, became the second most popular app in the Apple App Store. However, a vulnerability was soon discovered in Neon that allowed anyone to access phone numbers, call recordings, and transcripts of users' conversations. Neon Mobile's
official website states that the company pays 30 cents per minute for calls to other Neon users, and up to $30 per day for calls to other people. The app also offered rewards for attracting new users. The app's developers sell the collected data to AI companies, as calls help train, improve, and test AI models. According to Appfigures, Neon was downloaded over 75,000 times on September 24, 2025 alone, so it's no surprise that it entered the top 5 apps in the Social Networking category in the US App Store. However, as TechCrunch reports , the app was soon temporarily disabled, and it's unknown when Neon will be back online. TechCrunch journalists discovered the vulnerability during a brief test. The problem was that Neon's servers didn't restrict authorized users from accessing other accounts' data. The journalists created a new account on a separate iPhone, verified their phone number, and used the network traffic analysis tool Burp Suite to understand how Neon interacted with its servers. After several test calls, the app displayed a list of recent calls and the amount of money each call brought in. Traffic analysis revealed text transcripts of the conversations, as well as web addresses of the audio files, which could be accessed simply by accessing the link. The screenshot below shows a fragment of the transcript of a test call between two TechCrunch journalists, confirming that the recording was working. The problem was compounded by the fact that Neon's servers allowed other users to access the call recordings and their transcripts. In several cases, researchers were able to obtain data on the app's users' most recent calls, including links to audio files and text transcripts (only Neon users were recorded, not their callers). Furthermore, the app's servers provided a list of any user's most recent calls, along with all metadata: phone numbers of both parties, the time and duration of the call, and the amount earned from recording the conversation. Journalists note that an examination of several recordings revealed that Neon users were calling real people, secretly recording the conversations to profit from the app.
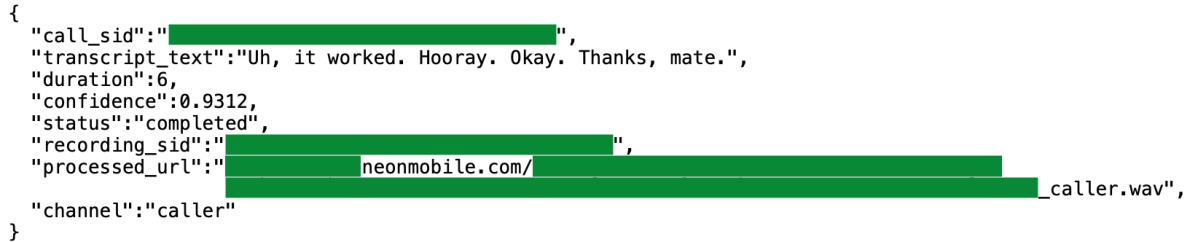
The researchers reported this dangerous discovery to the app's founder, Alex Kiam. After Kiam, who had previously not responded to the publication's inquiries, shut down Neon's servers and began notifying users that the app had been suspended. However, the message made no mention of the vulnerability discovered, which made phone numbers, recordings, and transcripts of conversations accessible to anyone.
[td]"Your privacy is our top priority. We want to ensure it remains fully protected, even during periods of rapid growth. Therefore, we are temporarily disabling the app to add additional layers of security," the notice read.[/td]Neon's developers did not respond to journalists' questions about whether the app underwent security testing before launch. It is also unknown whether the company has technical means (such as logs) to determine whether this vulnerability was previously discovered or whether user data was stolen.
TechCrunch notes that it is unknown when Neon will be back online or whether app store moderators will address the incident. Representatives from Apple and Google did not respond to the publication's request for comment or whether Neon complies with their platforms' policies.
official website states that the company pays 30 cents per minute for calls to other Neon users, and up to $30 per day for calls to other people. The app also offered rewards for attracting new users. The app's developers sell the collected data to AI companies, as calls help train, improve, and test AI models. According to Appfigures, Neon was downloaded over 75,000 times on September 24, 2025 alone, so it's no surprise that it entered the top 5 apps in the Social Networking category in the US App Store. However, as TechCrunch reports , the app was soon temporarily disabled, and it's unknown when Neon will be back online. TechCrunch journalists discovered the vulnerability during a brief test. The problem was that Neon's servers didn't restrict authorized users from accessing other accounts' data. The journalists created a new account on a separate iPhone, verified their phone number, and used the network traffic analysis tool Burp Suite to understand how Neon interacted with its servers. After several test calls, the app displayed a list of recent calls and the amount of money each call brought in. Traffic analysis revealed text transcripts of the conversations, as well as web addresses of the audio files, which could be accessed simply by accessing the link. The screenshot below shows a fragment of the transcript of a test call between two TechCrunch journalists, confirming that the recording was working. The problem was compounded by the fact that Neon's servers allowed other users to access the call recordings and their transcripts. In several cases, researchers were able to obtain data on the app's users' most recent calls, including links to audio files and text transcripts (only Neon users were recorded, not their callers). Furthermore, the app's servers provided a list of any user's most recent calls, along with all metadata: phone numbers of both parties, the time and duration of the call, and the amount earned from recording the conversation. Journalists note that an examination of several recordings revealed that Neon users were calling real people, secretly recording the conversations to profit from the app.


The researchers reported this dangerous discovery to the app's founder, Alex Kiam. After Kiam, who had previously not responded to the publication's inquiries, shut down Neon's servers and began notifying users that the app had been suspended. However, the message made no mention of the vulnerability discovered, which made phone numbers, recordings, and transcripts of conversations accessible to anyone.
TechCrunch notes that it is unknown when Neon will be back online or whether app store moderators will address the incident. Representatives from Apple and Google did not respond to the publication's request for comment or whether Neon complies with their platforms' policies.
