- 888
- 245
Researchers from Check Point report that the developers of the Lumma infostealer are trying to resume operations and conduct business as usual after law enforcement reported the seizure of thousands of domains and part of the malware infrastructure.
Recall that in mid-May 2025, law enforcement agencies and information security specialists confiscated about 2,300 domains associated with Lumma activities.
Microsoft, Cloudflare, ESET, CleanDNS, Bitsight, Lumen, GMO Registry and the international law firm Orrick took part in a coordinated attack on the malware infrastructure.
At the same time, the US Department of Justice seized five domains associated with Lumma control panels, and the European Cybercrime Center (EC3) at Europol and the Japanese Cybercrime Center (JC3) helped confiscate Lumma infrastructure located in Europe and Japan.
At the time, it was emphasized that more than 1,300 domains confiscated or transferred to Microsoft would be sinkholed. In this way, the company's specialists planned to collect and provide useful information to partners from the public and private sectors.
As reported by the Lumma developers, the authorities were unable to confiscate the stealer's main server due to its geographical location. However, they successfully penetrated it using a previously unknown vulnerability in the Integrated Dell Remote Access Controller (iDRAC). As a result, law enforcement was able to clean the server and erase backups.

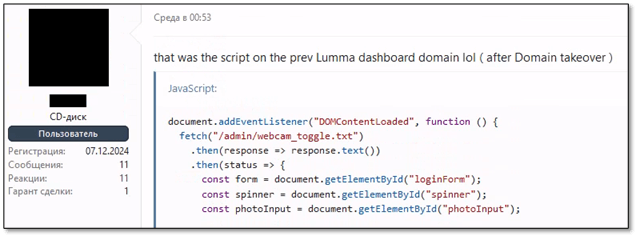
Although the developers emphasize that they did not log the IP addresses of their clients, law enforcement created a phishing login page that collected credentials and digital fingerprints of Lumma clients. A JavaScript snippet was also embedded on the page that attempted to access visitors' webcams.
As Check Point researchers now report, the law enforcement operation definitely created difficulties for the hacker group behind Lumma, but the stealer was not destroyed. Thus, according to experts, the group's control servers continue to operate, the amount of information stolen by Lumma continues to grow, and this data continues to be sold on shadow marketplaces.
[td]"Check Point Research has observed significant efforts by Lumma developers to fully restore information theft activity and continue business as usual," the researchers report.[/td]It is noted that the government's attack on Lumma's infrastructure has generated numerous discussions on hacker forums, where participants express uncertainty about Lumma's future. At the same time, it is claimed that none of the developers associated with Lumma have been arrested.
According to analysts, the further fate of the malware largely depends on psychological and reputational factors, since Lumma's technical capabilities are currently limited, but the stealer has not been destroyed.
[td]“It may turn out that the suspicions sown among Lumma’s partners and customers will not be so easy to overcome,” Check Point admits.[/td]
Recall that in mid-May 2025, law enforcement agencies and information security specialists confiscated about 2,300 domains associated with Lumma activities.
Microsoft, Cloudflare, ESET, CleanDNS, Bitsight, Lumen, GMO Registry and the international law firm Orrick took part in a coordinated attack on the malware infrastructure.
At the same time, the US Department of Justice seized five domains associated with Lumma control panels, and the European Cybercrime Center (EC3) at Europol and the Japanese Cybercrime Center (JC3) helped confiscate Lumma infrastructure located in Europe and Japan.
At the time, it was emphasized that more than 1,300 domains confiscated or transferred to Microsoft would be sinkholed. In this way, the company's specialists planned to collect and provide useful information to partners from the public and private sectors.
As reported by the Lumma developers, the authorities were unable to confiscate the stealer's main server due to its geographical location. However, they successfully penetrated it using a previously unknown vulnerability in the Integrated Dell Remote Access Controller (iDRAC). As a result, law enforcement was able to clean the server and erase backups.

Although the developers emphasize that they did not log the IP addresses of their clients, law enforcement created a phishing login page that collected credentials and digital fingerprints of Lumma clients. A JavaScript snippet was also embedded on the page that attempted to access visitors' webcams.

As Check Point researchers now report, the law enforcement operation definitely created difficulties for the hacker group behind Lumma, but the stealer was not destroyed. Thus, according to experts, the group's control servers continue to operate, the amount of information stolen by Lumma continues to grow, and this data continues to be sold on shadow marketplaces.
According to analysts, the further fate of the malware largely depends on psychological and reputational factors, since Lumma's technical capabilities are currently limited, but the stealer has not been destroyed.
