- 864
- 43
Extension for Burp Suite which uses AWS API Gateway to change your IP on every request.
Description
This extension allows you to easily spin up API Gateways across multiple regions. All the Burp Suite traffic for the targeted host is then routed through the API Gateway endpoints which causes the IP to be different on each request. (There is a chance for recycling of IPs but this is pretty low and the more regions you use the less of a chance.)
This is useful to bypass different kinds of IP blocking like bruteforce protection that blocks based on IP, API rate limiting based on IP or WAF blocking based on IP etc.
Usage
- Setup Jython in Burp Suite
- Install the boto3 module for Python 2
- pip install boto3
- Ensure you have a set of AWS keys that have full access to the API Gateway service. This is available through the free tier of AWS.
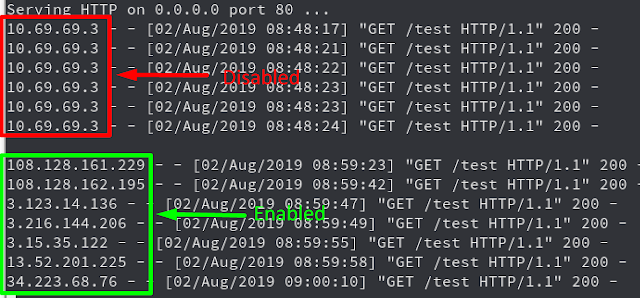
- Insert the credentials into the fields.
- Insert the target domain you wish to target.
- Select HTTPS if the domain is hosted over HTTPS.
- Select all the regions you want to use.(The more you use the larger the IP pool will be)
- Click "Enable".
- Once you are done ensure you click disable to delete all the resources which were started.
The Burp UI
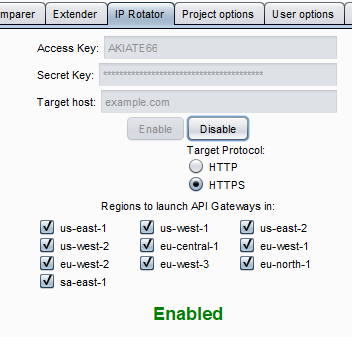
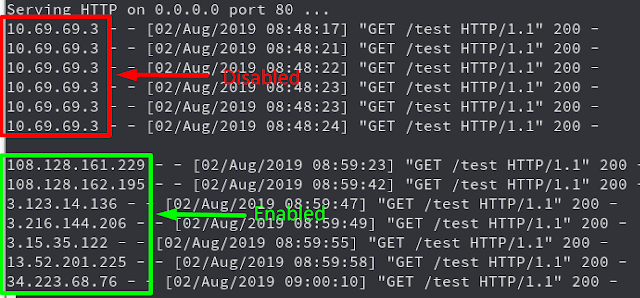
Example of how the requests look
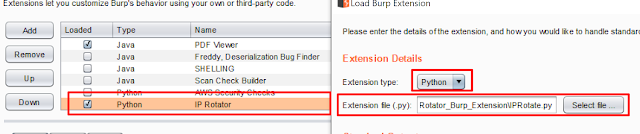
Setup
Make sure you have Jython installed and add IPRotate.py through the Burp Extension options.
Previous Research
After releasing this extension it was pointed out that there has been other research in this area using AWS API Gateway to hide an IP address. There is some awesome research and tools by @ustayready @ryHanson and @rmikehodges using this technique.
Be sure to check them out too:
https://github.com/ustayready/fireprox
https://github.com/rmikehodges/hideNsneak
Download IPRotate_Burp_Extension
