R
Realcarder
Guest
Fire Up Kali & Open a Browser
[FONT=&]Let's start by firing up Kali and opening a browser, such as Iceweasel, the default browser in Kali (EDB can be reached from any browser, in any operating system). If we use the default browser in Kali, we can see that there is a built-in shortcut to the "Exploit-DB" in the browser shortcut bar, as seen below.[/FONT]
[FONT=&]When we click on it, it takes us to the Exploit Database, as seen below.[/FONT]
[FONT=&]If you are not using Iceweasel and its built-in shortcut, you can navigate to Exploit-DB by typing www.exploit-db.com in the URL bar.[/FONT]Step 2Search the Exploit Database
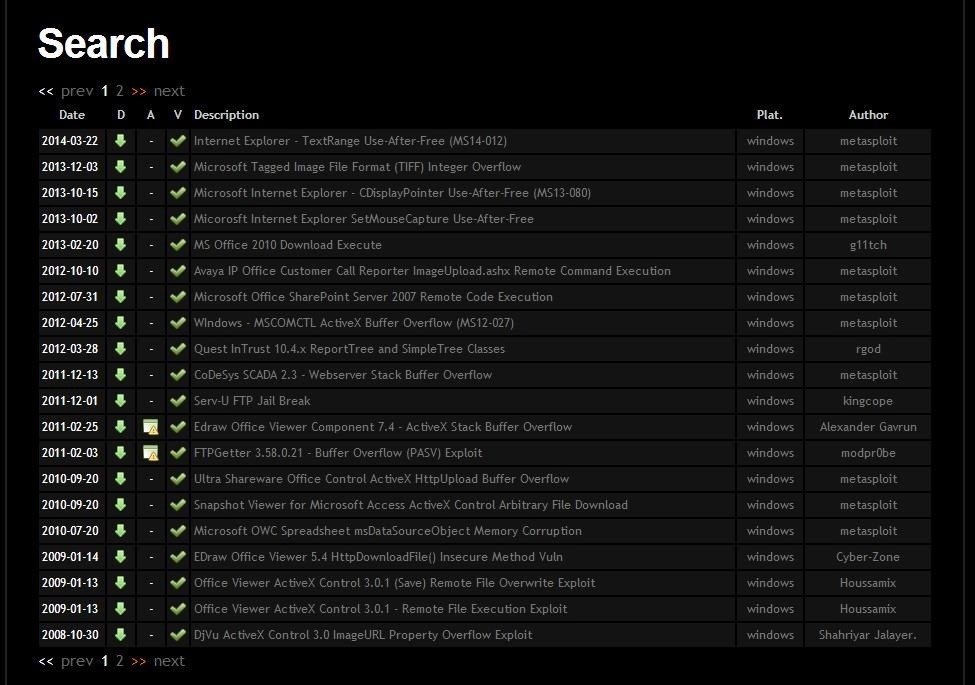
[FONT=&]If we look at the top menu bar in the Exploit Database website, second from the right is a menu item called "Search". When we click on it, it enables us to search the database of exploits and returns a search function screen similar to the screenshot below.[/FONT]
[FONT=&]Let's use this search function to find some recent Windows exploits (we are always looking for new Windows exploits, aren't we?). In the search function window, we can enter any of the following information;[/FONT]
[FONT=&]Let's start by firing up Kali and opening a browser, such as Iceweasel, the default browser in Kali (EDB can be reached from any browser, in any operating system). If we use the default browser in Kali, we can see that there is a built-in shortcut to the "Exploit-DB" in the browser shortcut bar, as seen below.[/FONT]
[FONT=&]When we click on it, it takes us to the Exploit Database, as seen below.[/FONT]
[FONT=&]If you are not using Iceweasel and its built-in shortcut, you can navigate to Exploit-DB by typing www.exploit-db.com in the URL bar.[/FONT]Step 2Search the Exploit Database
[FONT=&]If we look at the top menu bar in the Exploit Database website, second from the right is a menu item called "Search". When we click on it, it enables us to search the database of exploits and returns a search function screen similar to the screenshot below.[/FONT]
[FONT=&]Let's use this search function to find some recent Windows exploits (we are always looking for new Windows exploits, aren't we?). In the search function window, we can enter any of the following information;[/FONT]
[*=left]Description
[*=left]Free Text Search
[*=left]Author
[*=left]Platform (this is the operating system)
[*=left]Type
[*=left]Language
[*=left]Port
[*=left]OSVDB (the Open Source Vulnerability Database)
[*=left]CVE (Common Vulnerability and Exploits)