- 862
- 43
The creator of the RAT claims that the purpose of creating the RAT was solely to optimize and improve the work performed for the RAT. The author emphasizes that the main problem with most of the RAT is that they do not use encryption and request the inclusion of port forwarding on the victim device to control infected hosts. The developer offers his own tool, called RATAtack, which uses the Telegram protocol to support the encrypted channel of the victim and the channel creator, and does not require port forwarding, since the Telegram protocol provides a simple method of communication without first setting the port.
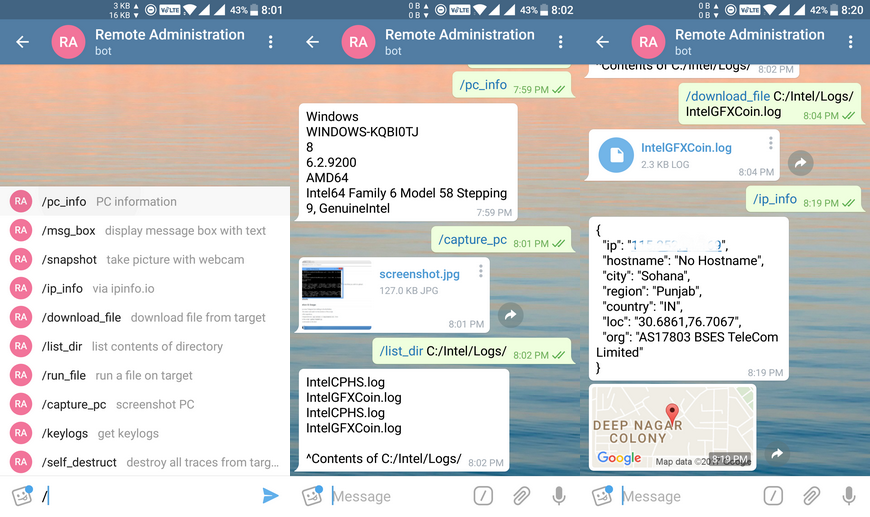
RAT works through bots in the Telegram
Before the appearance of RATatack, the RAT user must create a bot in Telegram, take the marker of this bot and put it in the RAT configuration file. After infecting the victim RATAttack, all hosts are connected to the bot channel. The owner of RATAttack can connect to the same channel and use simple instructions for managing RATatack clients in infected hosts. In accordance with the current version of RATAttack, the following commands are supported:
A mysterious “disclaimer” will keep the bad guys away.
Like most “dark” developers who create dual-purpose RATs, the developer called his creation the Remote Administration Tool . Even if some of the functions that he is currently working on are usually found in malicious trojans . They are not legal tools of remote administration, such as Teamviewer and others.
The developer also did not forget to execute the old number, and a mandatory “disclaimer” at the end of the RATAttack description , hoping to avoid the consequences that the attackers would cause, using its code, which is freely available to spy on companies, hacking companies, or keep dissidents under by observation.
Installation
RAT works through bots in the Telegram
Before the appearance of RATatack, the RAT user must create a bot in Telegram, take the marker of this bot and put it in the RAT configuration file. After infecting the victim RATAttack, all hosts are connected to the bot channel. The owner of RATAttack can connect to the same channel and use simple instructions for managing RATatack clients in infected hosts. In accordance with the current version of RATAttack, the following commands are supported:
The following are some of the features of the RATAttack, as well as those that are in development:Code:
/msg_box - Выводит окошко с текстом
/snapshot - Делает снимок с вебкамеры
/ip_info - Выводит IP
/download_file - Скачивает файл
/list_dir - Список файлов в текущей папке
/run_file - Выполняет файл
/capture_pc - Скрин рабочего стола
/keylogs - Кейлогер
/self_destruct - Уничтожает сам себя
- Running a keylogger on a PC target;
- Obtaining information about the PC goal, namely: Windows version, processor, etc .;
- Obtaining information about the IP address of the target and its approximate location on the map;
- Show a message box with custom text in the target computer;
- A list of all directories in the target computer;
- Local download of any file from the target computer in the background;
- Download local files to the target computer. Sending images, pdf, exe documents, and any other file to Telegram bot;
- Computer screenshots of the target;
- Execution of any file on the target computer.
- Self-destruction of RAT on the target computer;
- Webcam images (if available);
- Deleting files on the target computer
A mysterious “disclaimer” will keep the bad guys away.
Like most “dark” developers who create dual-purpose RATs, the developer called his creation the Remote Administration Tool . Even if some of the functions that he is currently working on are usually found in malicious trojans . They are not legal tools of remote administration, such as Teamviewer and others.

The developer also did not forget to execute the old number, and a mandatory “disclaimer” at the end of the RATAttack description , hoping to avoid the consequences that the attackers would cause, using its code, which is freely available to spy on companies, hacking companies, or keep dissidents under by observation.
Installation
Code:
git clone https://github.com/itJunky/RATAttack.git
cd RATAttack
pip install requirements.txt (для тех у кого дебиан или кали)
python RATAttack.py
