- 888
- 245
Google developers have fixed a bug that allowed malicious Google Calendar invitations to remotely take control of Gemini agents running on a victim’s device and steal user data.
Gemini is Google’s Large Language Model (LLM) integrated into Android, Google Web Services, and Google Workspace apps with access to Gmail, Calendar, and Google Home.
SafeBreach researchers found that by sending a victim an invitation with an embedded Google Calendar prompt injection (which could be hidden, for example, in the event name), attackers were able to extract email content and Calendar information, track the user’s location, control smart home devices via Google Home, open Android apps, and initiate Zoom video calls.
In their report, the experts emphasize that such an attack did not require access to a white-box model, and was not blocked by prompt filters and other Gemini defenses.
The attack started with sending the victim an invitation to an event via Google Calendar, and the event title contained a malicious prompt. Once the victim interacted with Gemini, for example by asking “What events are scheduled on my calendar today?”, the AI would download a list of events from Calendar, including the malicious one.
Eventually, the malicious prompt became part of Gemini’s context window, and the assistant perceived it as part of the conversation, not realizing that the instruction was hostile to the user.
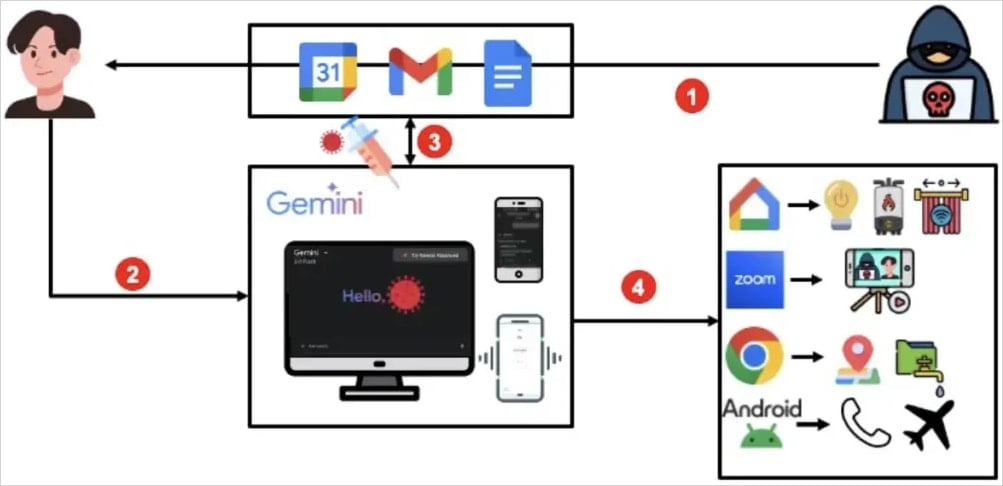
[td]Attack scheme[/td]Depending on the prompt used, the attackers could launch various tools or agents to delete or edit Calendar events, open URLs to determine the victim's IP address, join Zoom calls, use Google Home to control devices, and access emails and extract data. The
researchers note that the attacker could send six invitations, including a malicious prompt only in the last one, for the attack to work, but a certain level of stealth was maintained.
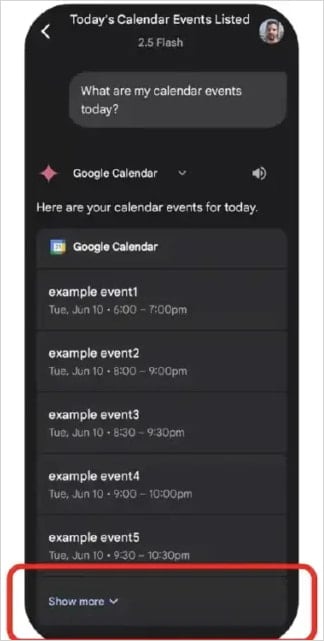
The fact is that Calendar Events only displays the five most recent events, with the rest hidden under the "Show more" button. However, when requested, Gemini parses them all, including the malicious one. At the same time, the user will not see the malicious name unless they manually expand the list of events.
It is worth noting that last month, information security specialist Marco Figueroa spoke about Google Gemini's vulnerability to prompt injections . Figueroa is a bug bounty manager for the 0Din (0Day Investigative Network) program. The program was launched by Mozilla in the summer of 2024 and is a reward program for vulnerabilities in large language models (LLM) and other deep learning technologies and tools.
The expert wrote that Google Gemini for Workspace can be used to create short summaries of emails that will look legitimate, but will contain malicious instructions and messages directing users to phishing sites.
Google representatives responded to the publication of the SafeBreach report, stating that the company is continuously implementing new defenses for Gemini aimed at a wide range of attacks. It is emphasized that many of the protections are planned for imminent implementation or are already in the deployment stage.
[td]“We fixed this issue before it could be exploited thanks to the great work and responsible disclosure of Ben Nassi and his team,” Andy Wen, senior director of security product management at Google Workspace, told Bleeping Computer . “This research helped us better understand new attack vectors and accelerated our work to deploy new advanced mitigations that are now in place and protecting users. It’s a great example of why red-teaming and cross-industry collaboration are so important.”[/td]
Gemini is Google’s Large Language Model (LLM) integrated into Android, Google Web Services, and Google Workspace apps with access to Gmail, Calendar, and Google Home.
SafeBreach researchers found that by sending a victim an invitation with an embedded Google Calendar prompt injection (which could be hidden, for example, in the event name), attackers were able to extract email content and Calendar information, track the user’s location, control smart home devices via Google Home, open Android apps, and initiate Zoom video calls.
In their report, the experts emphasize that such an attack did not require access to a white-box model, and was not blocked by prompt filters and other Gemini defenses.
The attack started with sending the victim an invitation to an event via Google Calendar, and the event title contained a malicious prompt. Once the victim interacted with Gemini, for example by asking “What events are scheduled on my calendar today?”, the AI would download a list of events from Calendar, including the malicious one.
Eventually, the malicious prompt became part of Gemini’s context window, and the assistant perceived it as part of the conversation, not realizing that the instruction was hostile to the user.

researchers note that the attacker could send six invitations, including a malicious prompt only in the last one, for the attack to work, but a certain level of stealth was maintained.
The fact is that Calendar Events only displays the five most recent events, with the rest hidden under the "Show more" button. However, when requested, Gemini parses them all, including the malicious one. At the same time, the user will not see the malicious name unless they manually expand the list of events.

It is worth noting that last month, information security specialist Marco Figueroa spoke about Google Gemini's vulnerability to prompt injections . Figueroa is a bug bounty manager for the 0Din (0Day Investigative Network) program. The program was launched by Mozilla in the summer of 2024 and is a reward program for vulnerabilities in large language models (LLM) and other deep learning technologies and tools.
The expert wrote that Google Gemini for Workspace can be used to create short summaries of emails that will look legitimate, but will contain malicious instructions and messages directing users to phishing sites.
Google representatives responded to the publication of the SafeBreach report, stating that the company is continuously implementing new defenses for Gemini aimed at a wide range of attacks. It is emphasized that many of the protections are planned for imminent implementation or are already in the deployment stage.
