- 901
- 246
F6 experts warn that attackers are disguising a banking Trojan for Android as premium and 18+ versions of popular apps, including YouTube and TikTok. Since early October 2025, analysts have identified more than 30 domains used to distribute this malware.
According to the experts, the attackers have created a network of malicious websites disguised as the brands of popular foreign video hosting sites YouTube and TikTok, which are difficult to access in Russia.
The malware is advertised as TikTok 18+, YouTube Max, YouTube Boost, YouTube Mega, YouTube Ultra, YouTube Plus, YouTube Ultima Edition, YouTube Pro, YouTube Advanced, and YouTube Plus, which promise ad-free viewing, 4K video, and functionality even with poor internet connection.

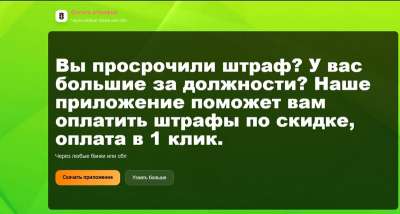
 Hackers are also disguising the malware as navigation apps, online traffic police maps, and a fine payment app.
Hackers are also disguising the malware as navigation apps, online traffic police maps, and a fine payment app.
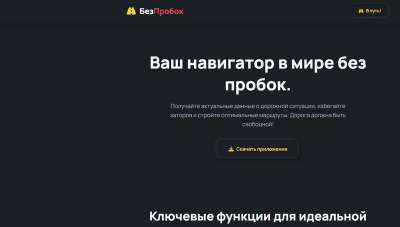
 The attackers' domains are registered in the .ru, .top, .pro, .fun, .life, .live, .icu, .com, and .cc zones. The website names use familiar brand names, as well as words like "ultra," "mega," "boost," "plus," and "max." All websites were indexed by Russian search engines.
The attackers' domains are registered in the .ru, .top, .pro, .fun, .life, .live, .icu, .com, and .cc zones. The website names use familiar brand names, as well as words like "ultra," "mega," "boost," "plus," and "max." All websites were indexed by Russian search engines.
[td]"We first recorded instances of such websites being created in the summer of 2025. In the fall, after the start of the school year, there was a surge in domain registrations, which attackers used to host malicious applications," comments Alexander Sapov, Senior Second-Line CERT Analyst at F6's Digital Risk Protection Department.[/td]Each such website is a landing page promising users no ads, 4K video downloads, background music playback, and, of course, access to blocked content. To obtain all this, users are prompted to download and install an APK file, which in fact contains malware.
The Trojan is capable of reading and sending SMS messages, making calls, collecting information about contacts and installed apps, obtaining network data, and launching automatically when the device is turned on. The malware can also display its own interface elements over other windows.
Ultimately, the attackers gain complete control over the device: they can monitor the victim's actions, secretly transfer data, and impersonate the user. The ultimate goal of these attacks is to steal the victim's financial data.
Currently, all domains of this malicious campaign have already been blocked, but experts do not rule out the possibility that the attackers may create new ones and continue their activity.
[td]"The slowdown of YouTube and the restriction of access to new TikTok videos in Russia have led to numerous proposals to circumvent the restrictions. This situation has inevitably been exploited by attackers who are disguising malicious apps as various popular programs," notes Alexander Bondal, Senior First-Line CERT Analyst at F6's Digital Risk Protection Department.[/td]
According to the experts, the attackers have created a network of malicious websites disguised as the brands of popular foreign video hosting sites YouTube and TikTok, which are difficult to access in Russia.
The malware is advertised as TikTok 18+, YouTube Max, YouTube Boost, YouTube Mega, YouTube Ultra, YouTube Plus, YouTube Ultima Edition, YouTube Pro, YouTube Advanced, and YouTube Plus, which promise ad-free viewing, 4K video, and functionality even with poor internet connection.




The Trojan is capable of reading and sending SMS messages, making calls, collecting information about contacts and installed apps, obtaining network data, and launching automatically when the device is turned on. The malware can also display its own interface elements over other windows.
Ultimately, the attackers gain complete control over the device: they can monitor the victim's actions, secretly transfer data, and impersonate the user. The ultimate goal of these attacks is to steal the victim's financial data.
Currently, all domains of this malicious campaign have already been blocked, but experts do not rule out the possibility that the attackers may create new ones and continue their activity.
