- 2,953
- 679
hishing is a form of fraud in which an attacker masquerades as a reputable entity or person in email or other communication channels. The attacker uses phishing emails to distribute malicious links or attachments that can perform a variety of functions, including the extraction of login credentials or account information from victims.
Phishing is popular with cybercriminals, as it is far easier to trick someone into clicking a malicious link in a seemingly legitimate phishing email than trying to break through a computer's defenses.
How phishing works?
Phishing attacks typically rely on social networking techniques applied to email or other electronic communication methods, including direct messages sent over social networks, SMS text messages and other instant messaging modes.
Phishers may use social engineering and other public sources of information, including social networks like LinkedIn, Facebook and Twitter, to gather background information about the victim's personal and work history, his interests, and his activities.
Pre-phishing attack reconnaissance can uncover names, job titles and email addresses of potential victims, as well as information about their colleagues and the names of key employees in their organizations. This information can then be used to craft a believable email. Targeted attacks, including those carried out by advanced persistent threat (APT) groups, typically begin with a phishing email containing a malicious link or attachment.
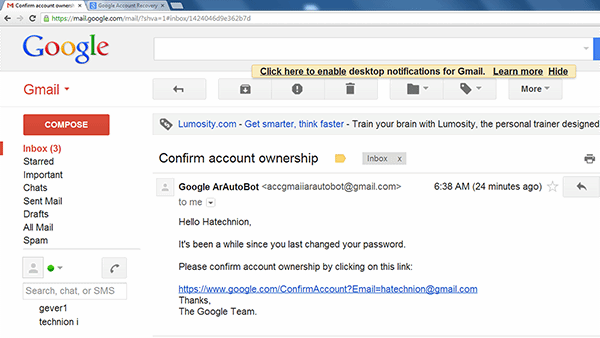
Although many phishing emails are poorly written and clearly fake, cybercriminal groups increasingly use the same techniques professional marketers use to identify the most effective types of messages -- the phishing hooks that get the highest open or click-through rate and the Facebook posts that generate the most likes. Phishing campaigns are often built around major events, holidays and anniversaries, or take advantage of breaking news stories, both true and fictitious.
Typically, a victim receives a message that appears to have been sent by a known contact or organization. The attack is carried out either through a malicious file attachment that contains phishing software, or through links connecting to malicious websites. In either case, the objective is to install malware on the user's device or direct the victim to a malicious website set up to trick them into divulging personal and financial information, such as passwords, account IDs or credit card details.
Successful phishing messages, usually represented as being from a well-known company, are difficult to distinguish from authentic messages: a phishing email can include corporate logos and other identifying graphics and data collected from the company being misrepresented. Malicious links within phishing messages are usually also designed to make it appear as though they go to the spoofed organization. The use of subdomains and misspelled URLs (typosquatting) are common tricks, as is the use of other link manipulation techniques.
Types of phishing
As defenders continue to educate their users in phishing defense and deploy anti-phishing strategies, cybercriminals continue to hone their skills at existing phishing attacks and roll out new types of phishing scams. Some of the more common types of phishing attacks include the following:
Spear phishing attacks are directed at specific individuals or companies, usually using information specific to the victim that has been gathered to more successfully represent the message as being authentic. Spear phishing emails might include references to coworkers or executives at the victim's organization, as well as the use of the victim's name, location or other personal information.
Whaling attacks are a type of spear phishing attack that specifically targets senior executives within an organization, often with the objective of stealing large sums. Those preparing a spear phishing campaign research their victims in detail to create a more genuine message, as using information relevant or specific to a target increases the chances of the attack being successful.
A typical whaling attack targets an employee with the ability to authorize payments, with the phishing message appearing to be a command from an executive to authorize a large payment to a vendor when, in fact, the payment would be made to the attackers.
Pharming is a type of phishing that depends on DNS cache poisoning to redirect users from a legitimate site to a fraudulent one, and tricking users into using their login credentials to attempt to log in to the fraudulent site.
Clone phishing attacks use previously delivered, but legitimate emails that contain either a link or an attachment. Attackers make a copy -- or clone -- of the legitimate email, replacing one or more links or attached files with malicious links or malware attachments. Because the message appears to be a duplicate of the original, legitimate email, victims can often be tricked into clicking the malicious link or opening the malicious attachment.
This technique is often used by attackers who have taken control of another victim's system. In this case, the attackers leverage their control of one system to pivot within an organization using email messages from a trusted sender known to the victims.
Phishers sometimes use the evil twin Wi-Fi attack by standing up a Wi-Fi access point and advertising it with a deceptive name that is similar to a legitimate access point. When victims connect to the evil twin Wi-Fi network, the attackers gain access to all the transmissions sent to or from victim devices, including user IDs and passwords. Attackers can also use this vector to target victim devices with their own fraudulent prompts for system credentials that appear to originate from legitimate systems.
Voice phishing, also known as vishing, is a form of phishing that occurs over voice communications media, including voice over IP (VoIP) or POTS (plain old telephone service). A typical vishing scam uses speech synthesis software to leave voicemails purporting to notify the victim of suspicious activity in a bank or credit account, and solicits the victim to respond to a malicious phone number to verify his identity -- thus compromising the victim's account credentials.
Another mobile device-oriented phishing attack, SMS phishing -- also sometimes called SMishing or SMShing -- uses text messaging to convince victims to disclose account credentials or to install malware.
Phishing techniques
Phishing attacks depend on more than simply sending an email to victims and hoping that they click on a malicious link or open a malicious attachment. Some phishing scams use JavaScript to place a picture of a legitimate URL over a browser's address bar. The URL revealed by hovering over an embedded link can also be changed by using JavaScript.
For most phishing attacks, whether carried out by email or some other medium, the objective is to get the victim to follow a link that appears to go to a legitimate web resource, but that actually takes the victim to a malicious web resource.
Phishing campaigns generally use one or more of a variety of link manipulation techniques to trick victims into clicking, which go by many different names. Link manipulation is also often referred to as URL hiding and is present in many common types of phishing, and used in different ways depending on the attacker and the target.
The simplest approach to link manipulation is to create a malicious URL that is displayed as if it were linking to a legitimate site or webpage, but to have the actual link point to a malicious web resource. Users knowledgeable enough to hover over the link to see where it goes can avoid accessing malicious pages.
Another phishing tactic is to use link shortening services like Bitly to hide the link destination. Victims have no way of knowing whether the shortened URLs point to legitimate web resources or to malicious resources.
Homograph spoofing depends on URLs that were created using different logical characters to read exactly like a trusted domain. For example, attackers may register domains that use different character sets that display close enough to established, well-known domains. Early examples of homograph spoofing include the use of the numerals 0 or 1 to replace the letters O or l.
For example, attackers might attempt to spoof the microsoft.com domain with m!crosoft.com, replacing the letter i with an exclamation mark. Malicious domains may also replace Latin characters with Cyrillic, Greek or other character sets that display similarly.
One way attackers bypass phishing defenses is through the use of filter evasion techniques. For example, most phishing defenses scan emails for particular phrases or terms common in phishing emails -- but by rendering all or part of the message as a graphical image, attackers can sometimes deliver their phishing emails.
Another phishing tactic relies on a covert redirect, where an open redirect vulnerability fails to check that a redirected URL is pointing to a trusted resource. In that case, the redirected URL is an intermediate, malicious page which solicits authentication information from the victim before forwarding the victim's browser to the legitimate site.
How to prevent phishing
Phishing defense begins with educating users to identify phishing messages, but there are other tactics that can cut down on successful attacks.
A gateway email filter can trap many mass-targeted phishing emails and reduce the number of phishing emails that reach users' inboxes.
Enterprise mail servers should make use of at least one email authentication standard to verify that inbound email is verified. These include the Sender Policy Framework(SPF) protocol, which can help reduce unsolicited email (spam); the DomainKeys Identified Mail (DKIM) protocol, which enables users to block all messages except for those that have been cryptographically signed; and the Domain-based Message Authentication, Reporting and Conformance (DMARC) protocol, which specifies that both SPF and DKIM be in use for inbound email, and which also provides a framework for using those protocols to block unsolicited email -- including phishing email -- more effectively.
A web security gateway can also provide another layer of defense by preventing users from reaching the target of a malicious link. They work by checking requested URLs against a constantly updated database of sites suspected of distributing malware.
There are several resources on the internet that provide help in combating phishing. The Anti-Phishing Working Group Inc. and the federal government's OnGuardOnline.gov website both provide advice on how to spot, avoid and report phishing attacks. Interactive security awareness training aids, such as Wombat Security Technologies' Anti-Phishing Training Suite or PhishMe, can help teach employees how to avoid phishing traps, while sites like FraudWatch International and MillerSmiles publish the latest phishing email subject lines that are circulating the internet.
How phishing got its name
The history of the term phishing is not entirely clear.
One common explanation for the term is that phishing is a homophone of fishing, and is so named because phishing scams use lures to catch unsuspecting victims, or fish.
Another explanation for the origin of phishing comes from a string -- <>< -- which is often found in AOL chat logs because those characters were a common HTML tag found in chat transcripts. Because it occurred so frequently in those logs, AOL admins could not productively search for it as a marker of potentially improper activity. Black hat hackers, the story goes, would replace any reference to illegal activity -- including credit card or account credentials theft -- with the string, which eventually gave the activity its name because the characters appear to be a simple rendering of a fish.
Phishing is popular with cybercriminals, as it is far easier to trick someone into clicking a malicious link in a seemingly legitimate phishing email than trying to break through a computer's defenses.
How phishing works?
Phishing attacks typically rely on social networking techniques applied to email or other electronic communication methods, including direct messages sent over social networks, SMS text messages and other instant messaging modes.
Phishers may use social engineering and other public sources of information, including social networks like LinkedIn, Facebook and Twitter, to gather background information about the victim's personal and work history, his interests, and his activities.
Pre-phishing attack reconnaissance can uncover names, job titles and email addresses of potential victims, as well as information about their colleagues and the names of key employees in their organizations. This information can then be used to craft a believable email. Targeted attacks, including those carried out by advanced persistent threat (APT) groups, typically begin with a phishing email containing a malicious link or attachment.

Although many phishing emails are poorly written and clearly fake, cybercriminal groups increasingly use the same techniques professional marketers use to identify the most effective types of messages -- the phishing hooks that get the highest open or click-through rate and the Facebook posts that generate the most likes. Phishing campaigns are often built around major events, holidays and anniversaries, or take advantage of breaking news stories, both true and fictitious.
Typically, a victim receives a message that appears to have been sent by a known contact or organization. The attack is carried out either through a malicious file attachment that contains phishing software, or through links connecting to malicious websites. In either case, the objective is to install malware on the user's device or direct the victim to a malicious website set up to trick them into divulging personal and financial information, such as passwords, account IDs or credit card details.
Successful phishing messages, usually represented as being from a well-known company, are difficult to distinguish from authentic messages: a phishing email can include corporate logos and other identifying graphics and data collected from the company being misrepresented. Malicious links within phishing messages are usually also designed to make it appear as though they go to the spoofed organization. The use of subdomains and misspelled URLs (typosquatting) are common tricks, as is the use of other link manipulation techniques.
Types of phishing
As defenders continue to educate their users in phishing defense and deploy anti-phishing strategies, cybercriminals continue to hone their skills at existing phishing attacks and roll out new types of phishing scams. Some of the more common types of phishing attacks include the following:
Spear phishing attacks are directed at specific individuals or companies, usually using information specific to the victim that has been gathered to more successfully represent the message as being authentic. Spear phishing emails might include references to coworkers or executives at the victim's organization, as well as the use of the victim's name, location or other personal information.
Whaling attacks are a type of spear phishing attack that specifically targets senior executives within an organization, often with the objective of stealing large sums. Those preparing a spear phishing campaign research their victims in detail to create a more genuine message, as using information relevant or specific to a target increases the chances of the attack being successful.
A typical whaling attack targets an employee with the ability to authorize payments, with the phishing message appearing to be a command from an executive to authorize a large payment to a vendor when, in fact, the payment would be made to the attackers.
Pharming is a type of phishing that depends on DNS cache poisoning to redirect users from a legitimate site to a fraudulent one, and tricking users into using their login credentials to attempt to log in to the fraudulent site.
Clone phishing attacks use previously delivered, but legitimate emails that contain either a link or an attachment. Attackers make a copy -- or clone -- of the legitimate email, replacing one or more links or attached files with malicious links or malware attachments. Because the message appears to be a duplicate of the original, legitimate email, victims can often be tricked into clicking the malicious link or opening the malicious attachment.
This technique is often used by attackers who have taken control of another victim's system. In this case, the attackers leverage their control of one system to pivot within an organization using email messages from a trusted sender known to the victims.
Phishers sometimes use the evil twin Wi-Fi attack by standing up a Wi-Fi access point and advertising it with a deceptive name that is similar to a legitimate access point. When victims connect to the evil twin Wi-Fi network, the attackers gain access to all the transmissions sent to or from victim devices, including user IDs and passwords. Attackers can also use this vector to target victim devices with their own fraudulent prompts for system credentials that appear to originate from legitimate systems.
Voice phishing, also known as vishing, is a form of phishing that occurs over voice communications media, including voice over IP (VoIP) or POTS (plain old telephone service). A typical vishing scam uses speech synthesis software to leave voicemails purporting to notify the victim of suspicious activity in a bank or credit account, and solicits the victim to respond to a malicious phone number to verify his identity -- thus compromising the victim's account credentials.
Another mobile device-oriented phishing attack, SMS phishing -- also sometimes called SMishing or SMShing -- uses text messaging to convince victims to disclose account credentials or to install malware.
Phishing techniques
Phishing attacks depend on more than simply sending an email to victims and hoping that they click on a malicious link or open a malicious attachment. Some phishing scams use JavaScript to place a picture of a legitimate URL over a browser's address bar. The URL revealed by hovering over an embedded link can also be changed by using JavaScript.
For most phishing attacks, whether carried out by email or some other medium, the objective is to get the victim to follow a link that appears to go to a legitimate web resource, but that actually takes the victim to a malicious web resource.
Phishing campaigns generally use one or more of a variety of link manipulation techniques to trick victims into clicking, which go by many different names. Link manipulation is also often referred to as URL hiding and is present in many common types of phishing, and used in different ways depending on the attacker and the target.
The simplest approach to link manipulation is to create a malicious URL that is displayed as if it were linking to a legitimate site or webpage, but to have the actual link point to a malicious web resource. Users knowledgeable enough to hover over the link to see where it goes can avoid accessing malicious pages.
Another phishing tactic is to use link shortening services like Bitly to hide the link destination. Victims have no way of knowing whether the shortened URLs point to legitimate web resources or to malicious resources.
Homograph spoofing depends on URLs that were created using different logical characters to read exactly like a trusted domain. For example, attackers may register domains that use different character sets that display close enough to established, well-known domains. Early examples of homograph spoofing include the use of the numerals 0 or 1 to replace the letters O or l.
For example, attackers might attempt to spoof the microsoft.com domain with m!crosoft.com, replacing the letter i with an exclamation mark. Malicious domains may also replace Latin characters with Cyrillic, Greek or other character sets that display similarly.
One way attackers bypass phishing defenses is through the use of filter evasion techniques. For example, most phishing defenses scan emails for particular phrases or terms common in phishing emails -- but by rendering all or part of the message as a graphical image, attackers can sometimes deliver their phishing emails.
Another phishing tactic relies on a covert redirect, where an open redirect vulnerability fails to check that a redirected URL is pointing to a trusted resource. In that case, the redirected URL is an intermediate, malicious page which solicits authentication information from the victim before forwarding the victim's browser to the legitimate site.
How to prevent phishing
Phishing defense begins with educating users to identify phishing messages, but there are other tactics that can cut down on successful attacks.
A gateway email filter can trap many mass-targeted phishing emails and reduce the number of phishing emails that reach users' inboxes.
Enterprise mail servers should make use of at least one email authentication standard to verify that inbound email is verified. These include the Sender Policy Framework(SPF) protocol, which can help reduce unsolicited email (spam); the DomainKeys Identified Mail (DKIM) protocol, which enables users to block all messages except for those that have been cryptographically signed; and the Domain-based Message Authentication, Reporting and Conformance (DMARC) protocol, which specifies that both SPF and DKIM be in use for inbound email, and which also provides a framework for using those protocols to block unsolicited email -- including phishing email -- more effectively.
A web security gateway can also provide another layer of defense by preventing users from reaching the target of a malicious link. They work by checking requested URLs against a constantly updated database of sites suspected of distributing malware.
There are several resources on the internet that provide help in combating phishing. The Anti-Phishing Working Group Inc. and the federal government's OnGuardOnline.gov website both provide advice on how to spot, avoid and report phishing attacks. Interactive security awareness training aids, such as Wombat Security Technologies' Anti-Phishing Training Suite or PhishMe, can help teach employees how to avoid phishing traps, while sites like FraudWatch International and MillerSmiles publish the latest phishing email subject lines that are circulating the internet.
How phishing got its name
The history of the term phishing is not entirely clear.
One common explanation for the term is that phishing is a homophone of fishing, and is so named because phishing scams use lures to catch unsuspecting victims, or fish.
Another explanation for the origin of phishing comes from a string -- <>< -- which is often found in AOL chat logs because those characters were a common HTML tag found in chat transcripts. Because it occurred so frequently in those logs, AOL admins could not productively search for it as a marker of potentially improper activity. Black hat hackers, the story goes, would replace any reference to illegal activity -- including credit card or account credentials theft -- with the string, which eventually gave the activity its name because the characters appear to be a simple rendering of a fish.
