- Joined
- May 15, 2016
- Messages
- 3,878
- Likes
- 2,573
- Points
- 1,730
To collect information about the victim, crooks used special “breakout” services in telegram channels or on underground hacker forums.

Employees of the Moscow criminal investigation department, with the assistance of Group-IB experts, detained the organizers of a criminal group specializing in re-issuing SIM cards and stealing money from customers of Russian banks. The group operated for several years, the damage from its activities is estimated at tens of millions of rubles, and even those who were in prison were their victims.
The peak of SIM card re-issuance fraud occurred in 2017-2018 - attackers hacked Instagram accounts, instant messengers, mail from well-known bloggers, entrepreneurs, show business and sports stars, and extorted a ransom to return access. A significant part of the crimes was related to gaining access to online banking and stealing money from the victim's bank account.
One of the criminal groups specialized in VIP-clients of Russian banks. To collect information about the victim, crooks used special “breakout” services in telegram channels or on underground hacker forums. As a rule, the owners of such services have established contacts with insiders in banks with a high level of access. So they can receive in real time not only the personal data of the client, but also the state of his bank account.
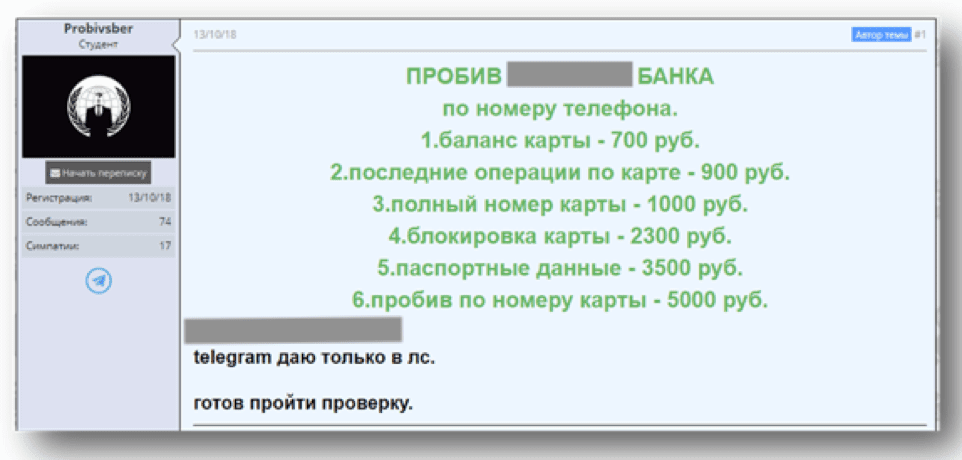
At the next stage, scammers used the services of an employee of an underground SIM card recovery service, also a rather popular service in the shadow segment of the Internet .. By making a fake power of attorney (the form costs about 1,500 rubles on the forums, they also use fake prints or print forms on a color printer), girl reissued a SIM-card in the salons of cellular communications in Moscow and Moscow region. As an identity card, the girl used a fake driver's license.
Immediately after the activation of the clone SIM card, the victim’s cellular communication disappeared, but at that moment the new owner of the SIM card sent to the bank requests for one-time access codes for mobile Internet banking. In some cases, the fraudster’s accomplice didn’t even bother sending the SIM card — she simply sent or dictated the received codes by phone. Money - an average of 50,000-100,000 rubles was withdrawn from the victim's account to third party accounts and cashed out in other cities, for example, in Samara, through a chain of transactions.
Moreover, if in 2017-2018 criminals withdrew large sums almost instantly, then, starting in 2019 - after the banks intensified the fight against fraud - it took them more time. Fraudsters could only make transactions a day after re-issuing SIM cards.
For this reason, fraudsters began to choose victims from among wealthy people who were in prison. A prerequisite is that the victim must have money in the account and mobile banking is connected. Recall that in the FSIN institutions, those under investigation and convicts are forbidden to use cellular communications, however, not only are cases of “smuggling” smartphones behind bars, but also the work of entire prison call centers, which resulted in a joint initiative by the Ministry of Internal Affairs, the FSB and the FSIN to block cellular communications in places imprisonment.
Numerous cases of embezzlement of money from customers of Russian banks became the reason for checking and initiating a criminal case. In the course of the investigation, employees of the Moscow MUR identified the organizers of the criminal group and attracted Group-IB experts. Two organizers of the group were detained in Solntsevo and Kommunarka, their accomplice from the “SIM-card recovery service” was in the Moscow Region. Another member of the group associated with cashing was caught in Samara. It is noteworthy that one of the members of the criminal group was tried for similar fraud with the re-issuance of SIM cards in 2014-2015, but when at large, he returned to his previous craft.
During the search, Group-IB operatives and specialists found numerous SIM-cards, laptops, smartphones and push-button telephones- “dialers”, fake documents - passports and driver’s licenses, as well as bank cards and SIM-cards attached to them, for which stolen money came . To store confidential information, scammers used flash cryptocontainers. The detainees confessed - they were charged with Part 4 under Article 159 of the Criminal Code of the Russian Federation (Fraud). In the case of several episodes, the number of victims is increasing, the total damage was estimated at several tens of millions of rubles
Detention Video:
“Unlike the well-known schemes with telephone fraud - vishing, when villains try to get a CVV or SMS code from a victim, the scheme with re-issuing SIM cards is not so massive and is aimed primarily at respectable wealthy clients,” says the head of the investigation department of Group- IB Sergey Lupanin . “More and more banks are agreeing with cellular operators on exchanging data to counter fraud: in the event of a re-issue of a SIM card, mobile banking is temporarily blocked and separate activation of online banking is required, but this rule is not yet valid for everyone.”
In order not to become a victim of a SIM card re-issuance scheme, Group-IB experts recommend writing a statement in the cabin of a mobile operator that re-issuing a SIM card is possible only with the personal presence of the subscriber. In this case, even if an attacker obtains a passport scan and falsifies a power of attorney, he will not be able to re-issue the SIM card and use it to access mobile banking. It is also important to clarify what the bank will do if the SIM card is reissued. If the user changes the mobile phone number himself, it is important to inform the bank about it, otherwise there is a risk that the new owner of the SIM card will be able to access the bank account.
__________________

Employees of the Moscow criminal investigation department, with the assistance of Group-IB experts, detained the organizers of a criminal group specializing in re-issuing SIM cards and stealing money from customers of Russian banks. The group operated for several years, the damage from its activities is estimated at tens of millions of rubles, and even those who were in prison were their victims.
The peak of SIM card re-issuance fraud occurred in 2017-2018 - attackers hacked Instagram accounts, instant messengers, mail from well-known bloggers, entrepreneurs, show business and sports stars, and extorted a ransom to return access. A significant part of the crimes was related to gaining access to online banking and stealing money from the victim's bank account.
One of the criminal groups specialized in VIP-clients of Russian banks. To collect information about the victim, crooks used special “breakout” services in telegram channels or on underground hacker forums. As a rule, the owners of such services have established contacts with insiders in banks with a high level of access. So they can receive in real time not only the personal data of the client, but also the state of his bank account.

At the next stage, scammers used the services of an employee of an underground SIM card recovery service, also a rather popular service in the shadow segment of the Internet .. By making a fake power of attorney (the form costs about 1,500 rubles on the forums, they also use fake prints or print forms on a color printer), girl reissued a SIM-card in the salons of cellular communications in Moscow and Moscow region. As an identity card, the girl used a fake driver's license.
Immediately after the activation of the clone SIM card, the victim’s cellular communication disappeared, but at that moment the new owner of the SIM card sent to the bank requests for one-time access codes for mobile Internet banking. In some cases, the fraudster’s accomplice didn’t even bother sending the SIM card — she simply sent or dictated the received codes by phone. Money - an average of 50,000-100,000 rubles was withdrawn from the victim's account to third party accounts and cashed out in other cities, for example, in Samara, through a chain of transactions.
Moreover, if in 2017-2018 criminals withdrew large sums almost instantly, then, starting in 2019 - after the banks intensified the fight against fraud - it took them more time. Fraudsters could only make transactions a day after re-issuing SIM cards.
For this reason, fraudsters began to choose victims from among wealthy people who were in prison. A prerequisite is that the victim must have money in the account and mobile banking is connected. Recall that in the FSIN institutions, those under investigation and convicts are forbidden to use cellular communications, however, not only are cases of “smuggling” smartphones behind bars, but also the work of entire prison call centers, which resulted in a joint initiative by the Ministry of Internal Affairs, the FSB and the FSIN to block cellular communications in places imprisonment.
Numerous cases of embezzlement of money from customers of Russian banks became the reason for checking and initiating a criminal case. In the course of the investigation, employees of the Moscow MUR identified the organizers of the criminal group and attracted Group-IB experts. Two organizers of the group were detained in Solntsevo and Kommunarka, their accomplice from the “SIM-card recovery service” was in the Moscow Region. Another member of the group associated with cashing was caught in Samara. It is noteworthy that one of the members of the criminal group was tried for similar fraud with the re-issuance of SIM cards in 2014-2015, but when at large, he returned to his previous craft.
During the search, Group-IB operatives and specialists found numerous SIM-cards, laptops, smartphones and push-button telephones- “dialers”, fake documents - passports and driver’s licenses, as well as bank cards and SIM-cards attached to them, for which stolen money came . To store confidential information, scammers used flash cryptocontainers. The detainees confessed - they were charged with Part 4 under Article 159 of the Criminal Code of the Russian Federation (Fraud). In the case of several episodes, the number of victims is increasing, the total damage was estimated at several tens of millions of rubles
Detention Video:
In order not to become a victim of a SIM card re-issuance scheme, Group-IB experts recommend writing a statement in the cabin of a mobile operator that re-issuing a SIM card is possible only with the personal presence of the subscriber. In this case, even if an attacker obtains a passport scan and falsifies a power of attorney, he will not be able to re-issue the SIM card and use it to access mobile banking. It is also important to clarify what the bank will do if the SIM card is reissued. If the user changes the mobile phone number himself, it is important to inform the bank about it, otherwise there is a risk that the new owner of the SIM card will be able to access the bank account.
__________________