- 820
- 222
Experts from CYFIRMA have published a detailed analysis of a new family of malware for Windows called TinkyWinkey, first noticed in late June 2025. This malware combines a keylogger and a system profiling tool, working as stealthily as possible and gaining a foothold in the system after reboot.
The malware consists of two modules: Tinky Service, a service responsible for the life cycle and autorun, and Winkey Keylogger, the main spyware core, which can be launched as a separate file or injected via DLL injection into trusted processes like explorer.exe.
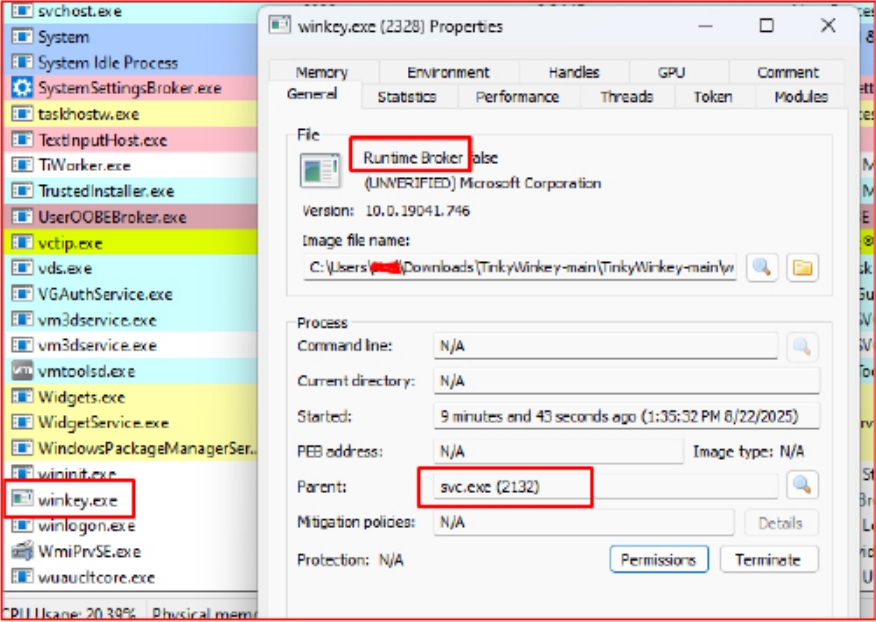
TinkyWinkey's special feature is its deep system reconnaissance. It collects OS fingerprints, processor information, memory size, and network parameters using low-level Windows APIs. This approach helps attackers make stolen data — passwords, correspondence, accounts — more valuable and convenient for subsequent attacks.
The keylogger intercepts all keystrokes, including special characters and input in different languages. Moreover, it tracks which window the user is working in, which allows passwords to be matched with specific applications - be it a browser, mail or online banking.
To save data, TinkyWinkey writes them to the logs_tw.txt file in the system temp folder, from where attackers can take the logs. Thanks to this, you can get not only passwords, but also chats, service records and other sensitive information.
CYFIRMA emphasizes : TinkyWinkey is one of the most secretive keyloggers of recent years. It combines autorun as a service, low-level keyboard interception and detailed system reconnaissance, which makes it a dangerous tool for cyber espionage.
The malware consists of two modules: Tinky Service, a service responsible for the life cycle and autorun, and Winkey Keylogger, the main spyware core, which can be launched as a separate file or injected via DLL injection into trusted processes like explorer.exe.

TinkyWinkey's special feature is its deep system reconnaissance. It collects OS fingerprints, processor information, memory size, and network parameters using low-level Windows APIs. This approach helps attackers make stolen data — passwords, correspondence, accounts — more valuable and convenient for subsequent attacks.
The keylogger intercepts all keystrokes, including special characters and input in different languages. Moreover, it tracks which window the user is working in, which allows passwords to be matched with specific applications - be it a browser, mail or online banking.
To save data, TinkyWinkey writes them to the logs_tw.txt file in the system temp folder, from where attackers can take the logs. Thanks to this, you can get not only passwords, but also chats, service records and other sensitive information.
CYFIRMA emphasizes : TinkyWinkey is one of the most secretive keyloggers of recent years. It combines autorun as a service, low-level keyboard interception and detailed system reconnaissance, which makes it a dangerous tool for cyber espionage.
