- 3,015
- 282
- 1,730
Palo Alto Networks analysts report the emergence of a new Linux malware, Auto-Color, which attacked universities and government organizations in North America and Asia between November and December 2024.
[td]“Once installed, Auto-Color provides attackers with full remote access to compromised machines, making it extremely difficult to remove without specialized software,” the researchers say.[/td]Auto-Color is named after the file that the malware's original payload is renamed to after installation. It is currently unknown how the backdoor penetrates victims' systems, but it is reported to require the victim to explicitly run it on a Linux machine.
What makes this malware unique is the arsenal of techniques it uses to evade detection. These include using seemingly innocuous file names (such as door or egg), hiding C&C communications, and using custom encryption algorithms to mask communication and configuration information.
Once run with root privileges, Auto-Color installs the libcext.so.2 malicious implant, copies itself and renames itself to /var/log/cross/auto-color, and modifies the /etc/ld.preload file to gain a foothold on the infected host.
[td]"If the current user does not have root rights, the malware will not continue installing the implant into the system. In subsequent stages, it will do everything possible without this library," the experts say.[/td]The mentioned implant is equipped with passive hook functions used in libc to intercept open() system calls, which the malware uses to hide C&C communications by modifying the /proc/net/tcp file, which contains information about all active network connections. It is noted that a similar tactic was previously used by another Linux malware, Symbiote , discovered in 2022.
In addition, the malware's uninstallation is prevented by protecting the /etc/ld.preload file from further modification or deletion.
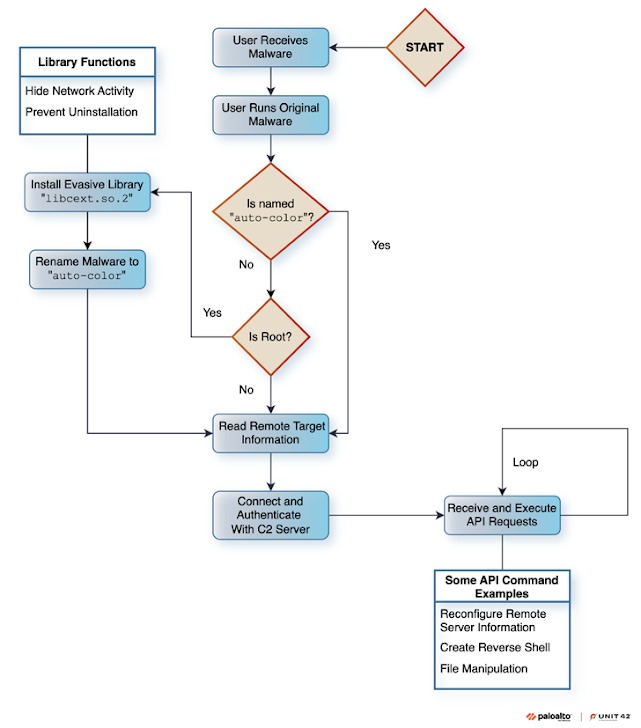
After the above actions, Auto-Color contacts the command and control server, allowing its operators to: launch a reverse shell, collect system information, create and modify files, run programs, use the infected machine as a proxy, and even destroy the malware using a special "switch" in the code. The latter function allows attackers to remove traces of infection from hacked machines, which can seriously complicate the investigation of the incident.
[td]"Once executed, the malware attempts to receive instructions from the command and control server, which is capable of creating reverse-shell backdoors in the victim's system. In doing so, the attackers separately compile and encrypt each IP address of the command and control server using their own algorithm," Palo Alto Networks notes.[/td]
What makes this malware unique is the arsenal of techniques it uses to evade detection. These include using seemingly innocuous file names (such as door or egg), hiding C&C communications, and using custom encryption algorithms to mask communication and configuration information.
Once run with root privileges, Auto-Color installs the libcext.so.2 malicious implant, copies itself and renames itself to /var/log/cross/auto-color, and modifies the /etc/ld.preload file to gain a foothold on the infected host.
In addition, the malware's uninstallation is prevented by protecting the /etc/ld.preload file from further modification or deletion.

After the above actions, Auto-Color contacts the command and control server, allowing its operators to: launch a reverse shell, collect system information, create and modify files, run programs, use the infected machine as a proxy, and even destroy the malware using a special "switch" in the code. The latter function allows attackers to remove traces of infection from hacked machines, which can seriously complicate the investigation of the incident.
