- 846
- 229
Palo Alto Networks experts discovered a previously unknown spyware program, LandFall , which exploited a zero-day vulnerability in Samsung devices. The attacks began at least in July 2024, and the malware was distributed via malicious images in the WhatsApp messenger.
According to the researchers, the malicious activity targeted individual users of Samsung Galaxy devices in the Middle East. In their attacks, the hackers exploited the critical vulnerability CVE-2025-21042 (CVSS score 8.8) in the libimagecodec.quram.so image processing library. This bug allowed arbitrary code execution on the target device via out-of-bounds writing. Samsung only fixed this issue in April 2025, by which time the malware had been active for approximately nine months.
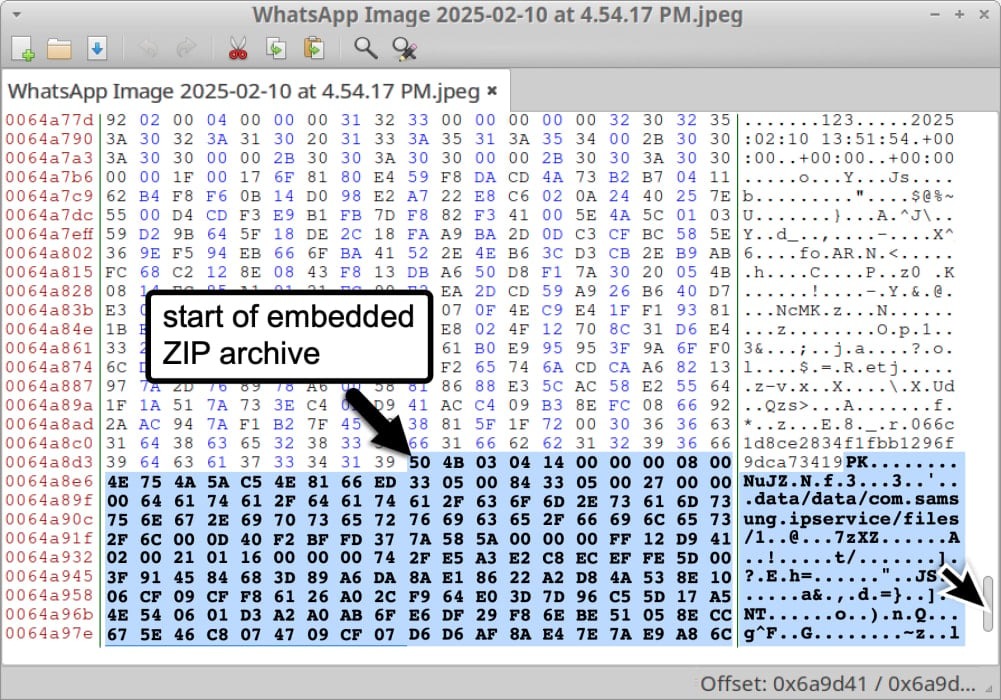
The attack began with the sending of a specially crafted .DNG image via WhatsApp. The image contained a ZIP archive containing malicious components. When a victim received such a file, the exploit would automatically trigger when the system processed the image.
[td]Built-in ZIP[/td]
Samples of malicious files used by LandFall began appearing on VirusTotal on July 23, 2024, and in all cases they were linked to WhatsApp, which served as the distribution channel. VirusTotal data indicates that victims were located in Iraq, Iran, Turkey, and Morocco.
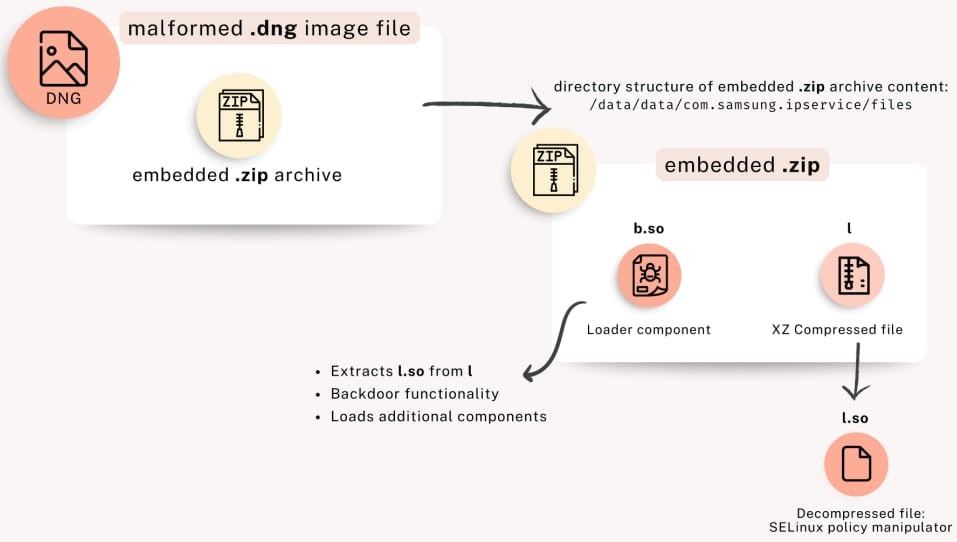
The LandFall spyware itself consists of two key modules: a loader (b.so), which can download and run additional components, and an SELinux policy modification component (l.so), which modifies security settings to escalate privileges and persist in the system.
[td]Attack scheme[/td]
LandFall collects a complete digital fingerprint of the device: IMEI, IMSI, SIM card number, account information, Bluetooth information, geolocation, and a list of installed apps. The spyware is also capable of:
Experts identified six command-and-control servers associated with this campaign, some of which have already been flagged as malicious by the Turkish CERT.
The researchers believe LandFall is a commercial targeted surveillance framework, but the exact attribution of the spyware has not yet been established. However, they note that the command-and-control infrastructure is similar to that used by the UAE-based Stealth Falcon hacker group. Furthermore, the name of the loader component (Bridge Head) matches characteristic component naming patterns commonly observed among spyware developers from companies such as NSO Group, Variston, Cytrox, and Quadream.
LandFall is not the only spyware trojan that exploits DNG images in its attacks. Similar attack chains have previously been used against iOS ( CVE-2025-43300 ) and WhatsApp ( CVE-2025-55177 ) users.
According to the researchers, the malicious activity targeted individual users of Samsung Galaxy devices in the Middle East. In their attacks, the hackers exploited the critical vulnerability CVE-2025-21042 (CVSS score 8.8) in the libimagecodec.quram.so image processing library. This bug allowed arbitrary code execution on the target device via out-of-bounds writing. Samsung only fixed this issue in April 2025, by which time the malware had been active for approximately nine months.
The attack began with the sending of a specially crafted .DNG image via WhatsApp. The image contained a ZIP archive containing malicious components. When a victim received such a file, the exploit would automatically trigger when the system processed the image.

[td]Built-in ZIP[/td]
Samples of malicious files used by LandFall began appearing on VirusTotal on July 23, 2024, and in all cases they were linked to WhatsApp, which served as the distribution channel. VirusTotal data indicates that victims were located in Iraq, Iran, Turkey, and Morocco.
The LandFall spyware itself consists of two key modules: a loader (b.so), which can download and run additional components, and an SELinux policy modification component (l.so), which modifies security settings to escalate privileges and persist in the system.

[td]Attack scheme[/td]
LandFall collects a complete digital fingerprint of the device: IMEI, IMSI, SIM card number, account information, Bluetooth information, geolocation, and a list of installed apps. The spyware is also capable of:
- record sound from the device's microphone and telephone conversations;
- track the victim's location in real time;
- steal photos, contacts, SMS and call logs;
- access files and browser history;
- load and execute additional modules;
- hide from detection and bypass protection.
Experts identified six command-and-control servers associated with this campaign, some of which have already been flagged as malicious by the Turkish CERT.
The researchers believe LandFall is a commercial targeted surveillance framework, but the exact attribution of the spyware has not yet been established. However, they note that the command-and-control infrastructure is similar to that used by the UAE-based Stealth Falcon hacker group. Furthermore, the name of the loader component (Bridge Head) matches characteristic component naming patterns commonly observed among spyware developers from companies such as NSO Group, Variston, Cytrox, and Quadream.
LandFall is not the only spyware trojan that exploits DNG images in its attacks. Similar attack chains have previously been used against iOS ( CVE-2025-43300 ) and WhatsApp ( CVE-2025-55177 ) users.
