- 892
- 245
Keep software updated
If you are running third-party software, on your WordPress website, such as plugins or themes, you should regularly update these. Updates often include security patches that fix vulnerabilities discovered by the community or security researchers.If you are running an older version of a theme that was previously vulnerable to XSS attacks, you can automatically protect against those attacks in the future by simply updating it when the developer releases a patch.
Web Application Firewall (WAF)
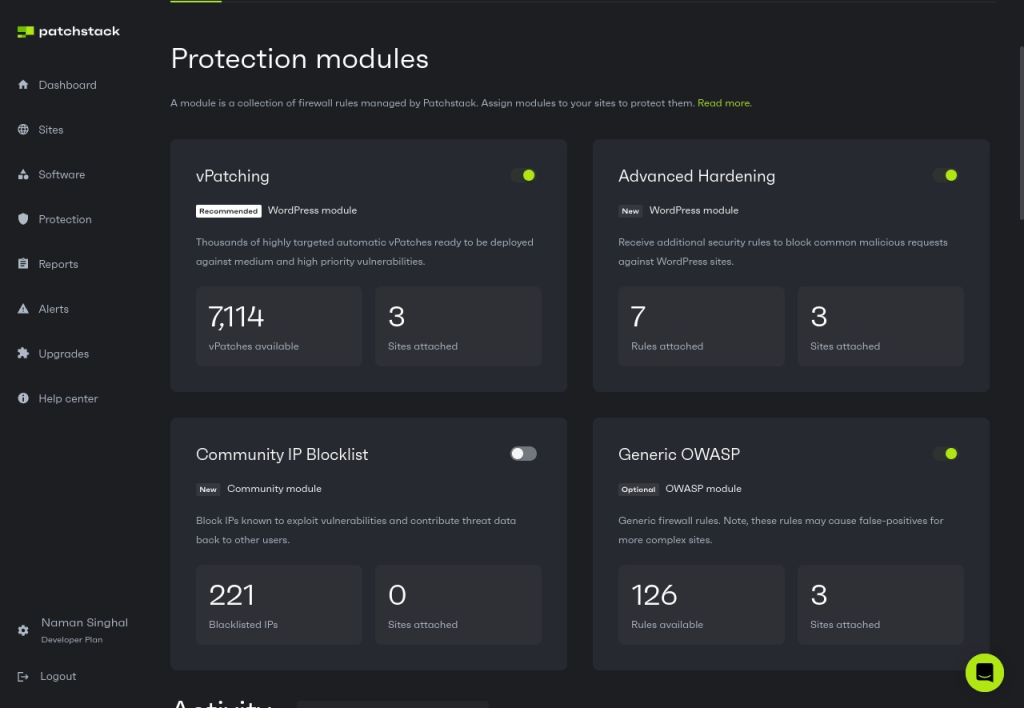
A Web Application Firewall is a protective barrier between your site and potential threats which filters incoming traffic and blocks malicious requests before they reach your application. If you properly configure the firewall on your website, then it can detect and block XSS attacks without human intervention.The simplest way to install a firewall on your WordPress site is to install Patchstack, a WordPress security solution.
In addition to generic OWASP modules, Patchstack now provides advanced hardening for WordPress. This means you can not only block XSS attacks but also stop any attacks specifically targeted at WordPress sites, such as privilege escalation attempts and malicious file uploads.
Data validation and sanitization
If you want to protect your site from XSS attacks, then there is one golden rule that you need to follow:"Never trust user input."
If you are developing a website, then we have some good news for you – WordPress provides all of the tools you need as a developer to protect your code from XSS security bugs.
If you are writing code that accepts values from users, you should sanitize it before using it anywhere in the code.
If your code is accepting a value from the browser, before you store it anywhere, you should sanitize the value using one of the many sanitization functions WordPress has. And before you output it as HTML, be sure you escape the value again using one of the many escaping functions WordPress provides.
Which function to use depends on the value you are expecting:
- If you are storing an email address, then use sanitize_email()
- If you are expecting the name of a file, then use sanitize_file_name()
- The most commonly used function is sanitize_text_field(), which is used for … you guessed it... text fields. However, sanitize_text_field() may not provide complete protection against XSS in all contexts, particularly within HTML attributes.
For example, in an input field like <input name="aaa" value="<?php echo sanitize_text_field($value);?>">, a malicious value of bbbb" onmouseover=alert(1)" could still trigger an XSS vulnerability when a user hovers over the input.
In such cases, esc_attr() is recommended to effectively sanitize and escape values within HTML attributes. - If you want to allow certain HTML elements and attributes while protecting against XSS attacks, then you can use the wp_kses() function to filter them out
Content Security Policy (CSP)
CSP is a security header that specifies a list of allowed resources for various content types. Whenever a web page is loaded, your browser requests a number of resources (scripts, styles, fonts, etc.) from the server. In most cases, these resources are fetched from the website server itself – but not always! Hackers can use the XSS vulnerability to fetch and execute a script from their own server on your website.One way to fix this is by blocking all third-party resources, but if you are using a CDN to serve the images on your site or if you are loading assets from a third-party site such as Google Fonts, then these would stop working as well.
The Content Security Policy allows you to specify which websites and domains are trustworthy. Read our post on hardening WordPress to learn more.
Wrapping up
XSS attacks pose a significant threat to WordPress websites as they allow hackers to execute arbitrary code on any website. By following the recommendations provided in this article, you can protect your website against XSS attacks. If you want to learn more about this topic, we recommend checking out the guide at Excess XSS.Protecting your WordPress website against XSS attacks is a good start, but it is not enough.
Every day, dozens, if not hundreds, of new vulnerabilities are discovered in popular WordPress themes and plugins.
If you want to stay ahead of attackers and receive a 48-hour early warning when a vulnerability is discovered, then you need to try Patchstack!
