Researchers at Seqrite Labs have identified a new malware campaign by a hacker group dubbed Silent Lynx. The group has previously targeted targets in Eastern Europe and Central Asia, including think tanks and banks involved in economic planning. The new campaigns target the National Bank of Kyrgyzstan and the country’s Ministry of Finance.
The attack begins with carefully crafted phishing emails designed to look like legitimate corporate correspondence. Victims receive an email purporting to be from a colleague or superior, containing a message marked as urgent.
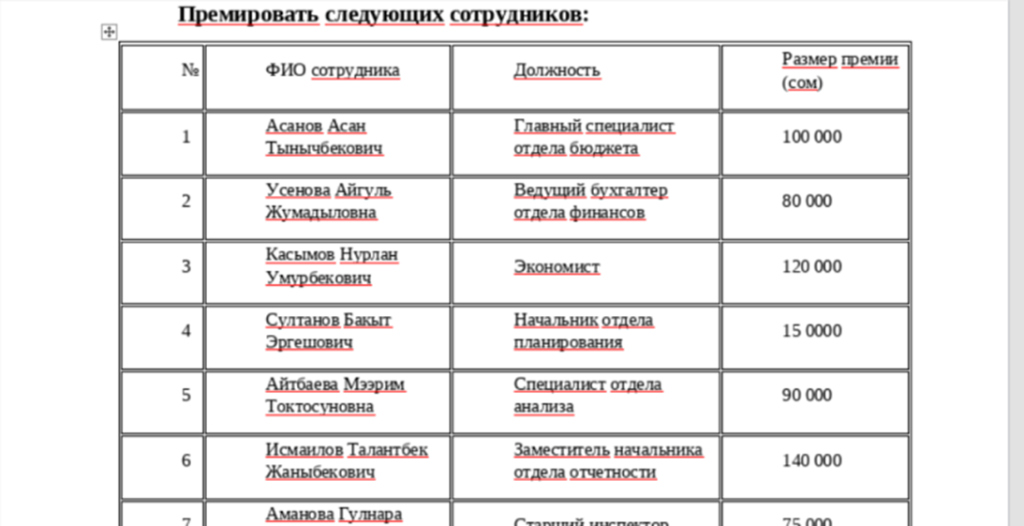
The email would claim that the archive contains important documents, such as bank statements or bonus notifications. To increase trust, real details about the employee or company were used, and the subject line, such as “Order on employee bonuses,” sounded official and believable.
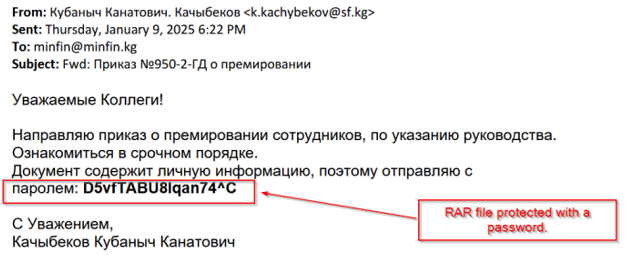
The RAR archive was password-protected, ostensibly to keep the data confidential, further convincing the recipient of its authenticity. The very topic of bonuses, especially in a corporate or government environment, naturally evokes interest and a desire to open an archive to learn the details. The archive contained two files: a fake document with an order for a bonus and a malicious executable file in the Golang language. The decorative documents included in the archives were of high quality and professionalism. In the case of the order, real positions, names and dates were used. This level of detail made the forgery invisible and the letter itself as convincing as possible. To the victim, this looked like standard work interaction, and opening the file seemed like a natural step. The executable file in Golang acted as a reverse shell, connecting to the command server. This allowed the attackers to remotely control the victim's system, continuing to collect confidential data. Thus, the use of social engineering and well-prepared fake documents made this attack especially dangerous, since even experienced employees could unwittingly open the archives and run malware, trusting plausible letters. Seqrite Labs has found commonalities between Silent Lynx and the well-known Kazakh group YoroTrooper. Both use PowerShell, similar tools and tactics, and their attacks are aimed at obtaining intelligence data. @ SecurityLab
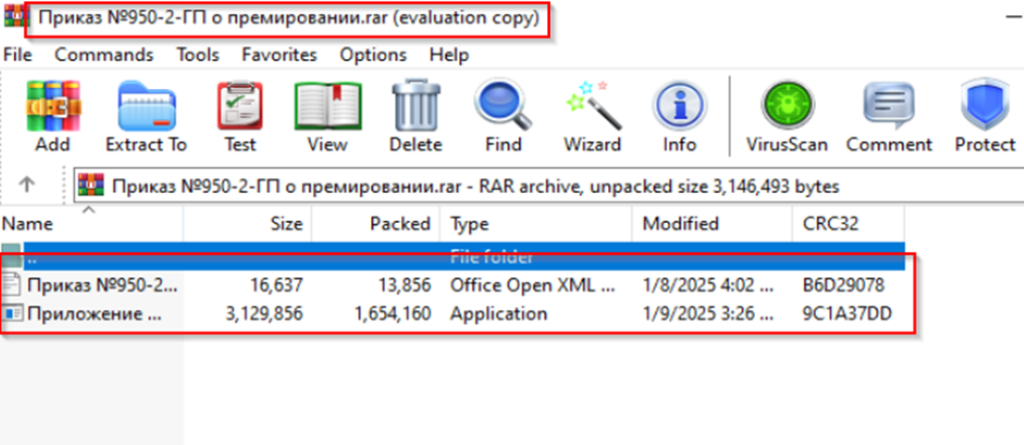
The attack begins with carefully crafted phishing emails designed to look like legitimate corporate correspondence. Victims receive an email purporting to be from a colleague or superior, containing a message marked as urgent.
The email would claim that the archive contains important documents, such as bank statements or bonus notifications. To increase trust, real details about the employee or company were used, and the subject line, such as “Order on employee bonuses,” sounded official and believable.

The RAR archive was password-protected, ostensibly to keep the data confidential, further convincing the recipient of its authenticity. The very topic of bonuses, especially in a corporate or government environment, naturally evokes interest and a desire to open an archive to learn the details. The archive contained two files: a fake document with an order for a bonus and a malicious executable file in the Golang language. The decorative documents included in the archives were of high quality and professionalism. In the case of the order, real positions, names and dates were used. This level of detail made the forgery invisible and the letter itself as convincing as possible. To the victim, this looked like standard work interaction, and opening the file seemed like a natural step. The executable file in Golang acted as a reverse shell, connecting to the command server. This allowed the attackers to remotely control the victim's system, continuing to collect confidential data. Thus, the use of social engineering and well-prepared fake documents made this attack especially dangerous, since even experienced employees could unwittingly open the archives and run malware, trusting plausible letters. Seqrite Labs has found commonalities between Silent Lynx and the well-known Kazakh group YoroTrooper. Both use PowerShell, similar tools and tactics, and their attacks are aimed at obtaining intelligence data. @ SecurityLab


