The Belsen Group has published configuration files, IP addresses, and VPN credentials for 15,000 FortiGate devices on the dark web, making this sensitive information freely available to other criminals.
The Belsen Group has only recently been spotted on social media and hacking forums. In an effort to promote themselves, the group created a dark web site where they published a dump of FortiGate device information for free, which is now freely available to other criminals.
[td]"As a positive start to the year for us and to make sure you remember our group's name, we are proud to announce our first operation: the publication of sensitive data from over 15,000 targets worldwide, both government and private. All of these devices were hacked and their data stolen," Belsen Group wrote on the hack forum.[/td]
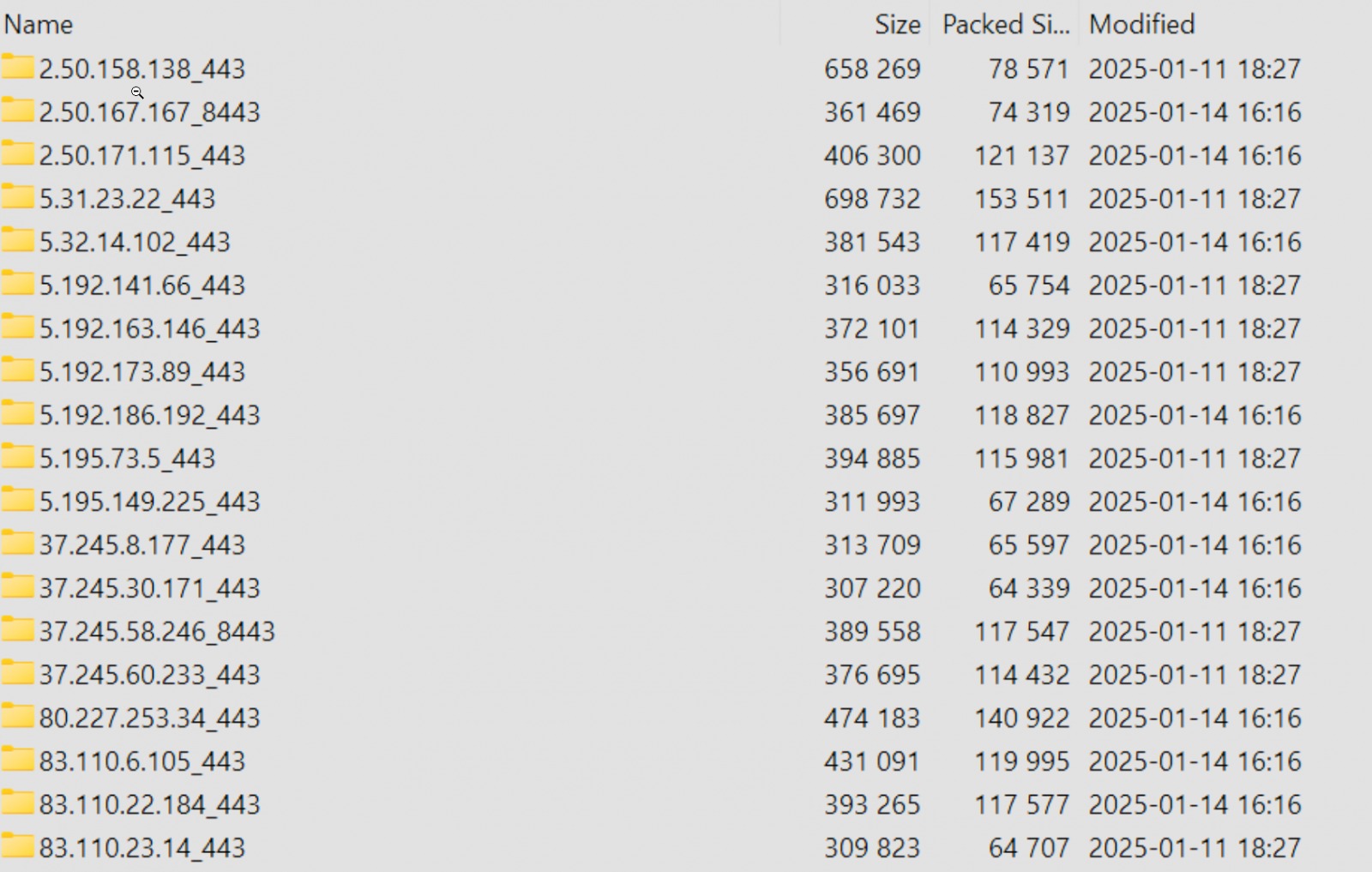
The leaked 1.6GB archive includes folders sorted by country. Within each folder are subfolders containing data for each FortiGate IP address. According to security researcher Kevin Beaumont, each folder with an IP address contains a configuration.conf file (a dump of the FortiGate configuration), as well as a vpn-passwords.txt file, which contains some passwords in clear text. The configuration files also contain sensitive data, including private keys and firewall rules. Beaumont believes that this leak is related to the zero-day vulnerability CVE-2022-40684 , which was actively exploited by attackers even before the release of patches.
[td]"I examined one of the devices at the affected organization and the artifacts on it indicated that CVE-2022-40684 had been exploited. I was also able to confirm that the usernames and passwords in the dump matched those on the device," Beaumont explains.[/td]The collected data, according to the researcher, dates back to October 2022, when the vulnerability was actively attacked. Why the dump was made publicly available only now, more than two years after these events, remains unclear.
Recall that in 2022, Fortinet warned that attackers were using CVE-2022-40684 to download configuration files from FortiGate devices and create new super_admin accounts named fortigate-tech-support. As Heise analysts reported at the time, the leak affected devices with FortiOS versions 7.0.0–7.0.6 and 7.2.0–7.2.2. At the same time, the CVE-2022-40684 issue had already been fixed in FortiOS 7.2.2, so it is not entirely clear how devices on this version were also affected.
Although the breach occurred in 2022, Beaumont warns that the published data may still contain critical information, including firewall rules and credentials. The expert said he plans to publish a list of the affected IP addresses so that FortiGate administrators can check if their devices are on the list.
The Belsen Group has only recently been spotted on social media and hacking forums. In an effort to promote themselves, the group created a dark web site where they published a dump of FortiGate device information for free, which is now freely available to other criminals.

The leaked 1.6GB archive includes folders sorted by country. Within each folder are subfolders containing data for each FortiGate IP address. According to security researcher Kevin Beaumont, each folder with an IP address contains a configuration.conf file (a dump of the FortiGate configuration), as well as a vpn-passwords.txt file, which contains some passwords in clear text. The configuration files also contain sensitive data, including private keys and firewall rules. Beaumont believes that this leak is related to the zero-day vulnerability CVE-2022-40684 , which was actively exploited by attackers even before the release of patches.

Recall that in 2022, Fortinet warned that attackers were using CVE-2022-40684 to download configuration files from FortiGate devices and create new super_admin accounts named fortigate-tech-support. As Heise analysts reported at the time, the leak affected devices with FortiOS versions 7.0.0–7.0.6 and 7.2.0–7.2.2. At the same time, the CVE-2022-40684 issue had already been fixed in FortiOS 7.2.2, so it is not entirely clear how devices on this version were also affected.
Although the breach occurred in 2022, Beaumont warns that the published data may still contain critical information, including firewall rules and credentials. The expert said he plans to publish a list of the affected IP addresses so that FortiGate administrators can check if their devices are on the list.
