- 37
- 2
Late last week, the Trust Wallet browser extension was compromised , resulting in the theft of $7 million in cryptocurrency from users. Now, it has become clear how exactly this attack was carried out and who may be behind it.
As a reminder, last week, users of the Trust Wallet Chrome extension began complaining en masse about the disappearance of cryptocurrency. It turned out that the issue was related to version 2.68, released on December 24, 2025, which turned out to be malicious.
Soon, Changpeng Zhao, founder of the Binance crypto exchange and owner of Trust Wallet, confirmed the theft of approximately $7 million from users and promised to fully compensate the victims. Trust Wallet developers also released a "clean" version of the wallet, 2.69, and recommended that everyone update immediately.
However, no details were released regarding the exact method of the attack. In fact, Trust Wallet developers did not disclose any technical details of the incident. Now, the situation is beginning to become clearer.
According to security specialists from SlowMist, the attackers injected malicious code directly into the source code of version 2.68 of the extension, rather than compromising third-party dependencies. The malware iterated through all wallets in the extension, requested a seed phrase for each one, decrypted it using the user's password, and then sent it to a server controlled by the attackers (api.metrics-trustwallet[.]com). The attackers used the legitimate PostHog analytics library to steal data by redirecting traffic to their server.
The metrics-trustwallet[.]com domain was registered on December 8, and the first requests were sent on December 21—three days before the release of the compromised version of the extension.
Furthermore, Trust Wallet CEO Eowyn Chen stated that the malicious update was not released through the company's internal process. According to her, hackers used a leaked API key for the Chrome Web Store and were able to release version 2.68, bypassing standard checks. The extension passed Google's moderation and was released on December 24 at 12:32 UTC.
According to Chen, the malicious domain has already been blocked, and the company has revoked all API keys and has already begun the refund process.
As reported by Bleeping Computer , in parallel with the release of the malicious version of Trust Wallet, the attackers launched a phishing campaign. Accounts appeared on the social network X directing users to the domain fix-trustwallet[.]com, which impersonated the official Trust Wallet website and offered to "fix the vulnerability" by installing a new version of the wallet.
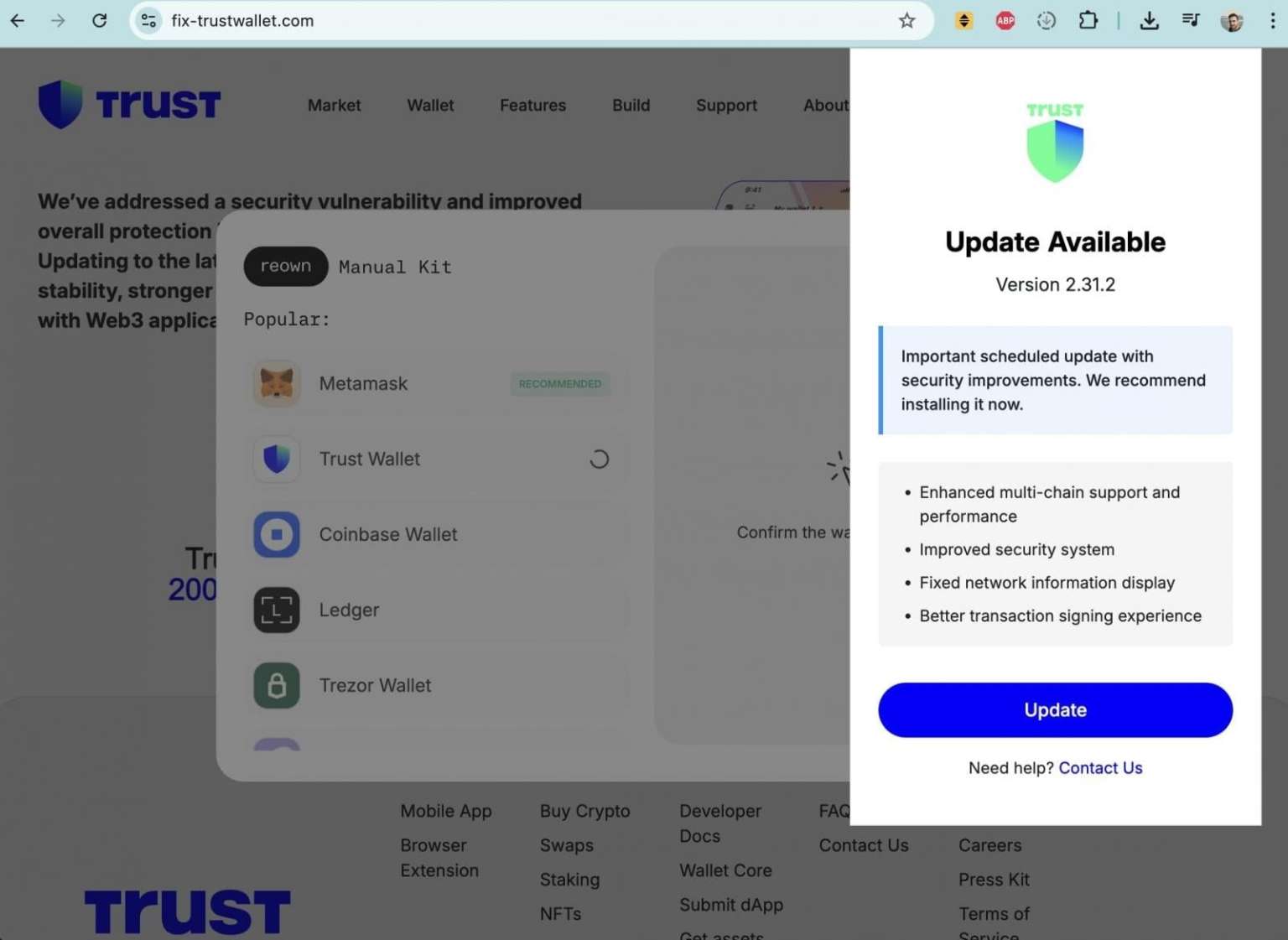
After clicking the refresh button, victims were shown a form requesting a seed phrase. Entering this data gave the attackers complete control of the wallet. The domain was registered with the same registrar as metrics-trustwallet[.]com, meaning the attacks were most likely related.
An analysis of blockchain transactions revealed that the hackers stole approximately $3 million in Bitcoin, $431 in Solana, and over $3 million in Ethereum. According to PeckShield specialists , the bulk of the funds (over $4 million) were withdrawn through centralized exchanges: approximately $3.3 million was sent to ChangeNOW, $340,000 to FixedFloat, and $447,000 to KuCoin. Another $2.8 million remains in the attackers' wallets.
SlowMist experts suggest that "government" hackers may be behind the attack—the attackers could have somehow gained control of Trust Wallet developers' devices or accessed the API long before December 8th.
It's also worth noting that Changpeng Zhao wrote that this attack could likely have been linked to insider activity, although there is no evidence to support this theory yet.
Last weekend, Trust Wallet representatives reiterated that they will compensate all victims. To do so, victims are asked to fill out a form on trustwallet-support.freshdesk.com, providing their contact email, country of residence, compromised wallet addresses, and transaction hashes.
The company also warns of phishing activity: fake compensation forms and fake support accounts have already appeared on Telegram. Trust Wallet reminds: official channels are the only secure way to communicate.
As a reminder, last week, users of the Trust Wallet Chrome extension began complaining en masse about the disappearance of cryptocurrency. It turned out that the issue was related to version 2.68, released on December 24, 2025, which turned out to be malicious.
Soon, Changpeng Zhao, founder of the Binance crypto exchange and owner of Trust Wallet, confirmed the theft of approximately $7 million from users and promised to fully compensate the victims. Trust Wallet developers also released a "clean" version of the wallet, 2.69, and recommended that everyone update immediately.
However, no details were released regarding the exact method of the attack. In fact, Trust Wallet developers did not disclose any technical details of the incident. Now, the situation is beginning to become clearer.
According to security specialists from SlowMist, the attackers injected malicious code directly into the source code of version 2.68 of the extension, rather than compromising third-party dependencies. The malware iterated through all wallets in the extension, requested a seed phrase for each one, decrypted it using the user's password, and then sent it to a server controlled by the attackers (api.metrics-trustwallet[.]com). The attackers used the legitimate PostHog analytics library to steal data by redirecting traffic to their server.
The metrics-trustwallet[.]com domain was registered on December 8, and the first requests were sent on December 21—three days before the release of the compromised version of the extension.
Furthermore, Trust Wallet CEO Eowyn Chen stated that the malicious update was not released through the company's internal process. According to her, hackers used a leaked API key for the Chrome Web Store and were able to release version 2.68, bypassing standard checks. The extension passed Google's moderation and was released on December 24 at 12:32 UTC.
According to Chen, the malicious domain has already been blocked, and the company has revoked all API keys and has already begun the refund process.
As reported by Bleeping Computer , in parallel with the release of the malicious version of Trust Wallet, the attackers launched a phishing campaign. Accounts appeared on the social network X directing users to the domain fix-trustwallet[.]com, which impersonated the official Trust Wallet website and offered to "fix the vulnerability" by installing a new version of the wallet.

After clicking the refresh button, victims were shown a form requesting a seed phrase. Entering this data gave the attackers complete control of the wallet. The domain was registered with the same registrar as metrics-trustwallet[.]com, meaning the attacks were most likely related.
An analysis of blockchain transactions revealed that the hackers stole approximately $3 million in Bitcoin, $431 in Solana, and over $3 million in Ethereum. According to PeckShield specialists , the bulk of the funds (over $4 million) were withdrawn through centralized exchanges: approximately $3.3 million was sent to ChangeNOW, $340,000 to FixedFloat, and $447,000 to KuCoin. Another $2.8 million remains in the attackers' wallets.
SlowMist experts suggest that "government" hackers may be behind the attack—the attackers could have somehow gained control of Trust Wallet developers' devices or accessed the API long before December 8th.
It's also worth noting that Changpeng Zhao wrote that this attack could likely have been linked to insider activity, although there is no evidence to support this theory yet.
Last weekend, Trust Wallet representatives reiterated that they will compensate all victims. To do so, victims are asked to fill out a form on trustwallet-support.freshdesk.com, providing their contact email, country of residence, compromised wallet addresses, and transaction hashes.
The company also warns of phishing activity: fake compensation forms and fake support accounts have already appeared on Telegram. Trust Wallet reminds: official channels are the only secure way to communicate.
