- Joined
- May 15, 2016
- Messages
- 4,021
- Likes
- 2,574
- Points
- 1,730
Over the past year, there has been a significant increase in the abuse of Cloudflare domains (ranging from 100% to 250%). Cloudflare Pages and Cloudflare Workers, typically used to deploy web pages and facilitate serverless computing, are increasingly being used for phishing and other malicious activity.
Fortra analysts say that the use of these domains is intended to increase the apparent legitimacy and effectiveness of malicious campaigns. That is, hackers are taking advantage of Cloudflare's brand, as well as the reliability of the service, low cost, and reverse proxying capabilities, which helps them evade detection.
Cloudflare Pages is a platform designed for front-end developers to create, deploy, and host fast and scalable sites directly on Cloudflare's CDN.
According to Fortra, attackers are actively using Cloudflare Pages to host intermediate phishing pages that redirect victims further to various malicious sites.
Fraudulent Cloudflare Pages typically lead users to links from malicious PDFs or phishing emails, which are undetectable by security solutions due to Cloudflare's reputation.

It is also noted that attackers use bccfoldering tactics to hide the recipients of emails and the scale of their malicious spam campaigns.
Cloudflare Workers, on the other hand, is a serverless computing platform that allows developers to build and deploy lightweight applications and scripts directly to Cloudflare's edge network. Under normal circumstances, Cloudflare Workers are used to deploy APIs, optimize content, implement custom firewalls and CAPTCHAs, automate tasks, and build microservices.
Attackers, however, use Cloudflare Workers to conduct DDoS attacks, deploy phishing sites, inject malicious scripts into victims' browsers, and brute-force passwords from other people's accounts.
Experts remind that to protect against phishing, including that which abuses legitimate services, it is always worth making sure that URLs are authentic, especially if the site asks to provide any confidential information.
In addition, activating additional security measures, such as two-factor authentication, can help prevent account takeover (even if credentials are compromised).
Fortra analysts say that the use of these domains is intended to increase the apparent legitimacy and effectiveness of malicious campaigns. That is, hackers are taking advantage of Cloudflare's brand, as well as the reliability of the service, low cost, and reverse proxying capabilities, which helps them evade detection.
Cloudflare Pages is a platform designed for front-end developers to create, deploy, and host fast and scalable sites directly on Cloudflare's CDN.
According to Fortra, attackers are actively using Cloudflare Pages to host intermediate phishing pages that redirect victims further to various malicious sites.
Fraudulent Cloudflare Pages typically lead users to links from malicious PDFs or phishing emails, which are undetectable by security solutions due to Cloudflare's reputation.

| Phishing email with link to pages.dev |
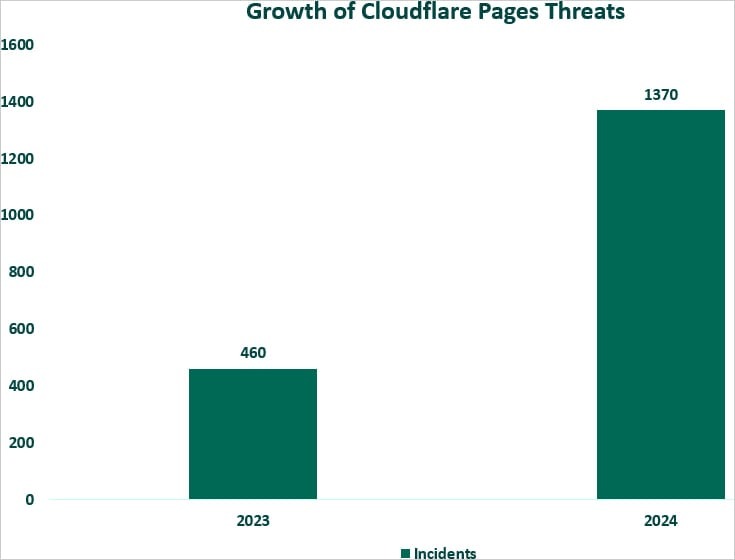
| “The Fortra team sees a 198 percent increase in phishing attacks using Cloudflare Pages, from 460 incidents in 2023 to 1,370 incidents as of October 2024,” the researchers report. “By the end of the year, the total number of attacks is expected to exceed 1,600, representing a 257 percent increase year-over-year (with an average of 137 incidents per month).” |

Cloudflare Workers, on the other hand, is a serverless computing platform that allows developers to build and deploy lightweight applications and scripts directly to Cloudflare's edge network. Under normal circumstances, Cloudflare Workers are used to deploy APIs, optimize content, implement custom firewalls and CAPTCHAs, automate tasks, and build microservices.
Attackers, however, use Cloudflare Workers to conduct DDoS attacks, deploy phishing sites, inject malicious scripts into victims' browsers, and brute-force passwords from other people's accounts.
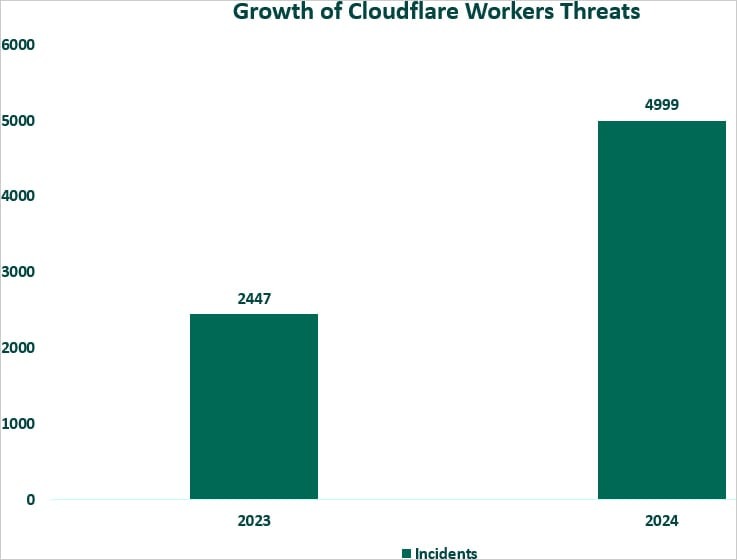
| “We have seen a 104 percent increase in phishing attacks related to the Cloudflare Workers platform, reaching 4,999 incidents this year, compared to 2,447 incidents in 2023,” Fortra said. “We are currently seeing an average of 499 incidents per month, and are expected to reach nearly 6,000 by the end of the year, representing a 145 percent increase over the previous year.” |

Experts remind that to protect against phishing, including that which abuses legitimate services, it is always worth making sure that URLs are authentic, especially if the site asks to provide any confidential information.
In addition, activating additional security measures, such as two-factor authentication, can help prevent account takeover (even if credentials are compromised).