- 3,002
- 280
- 1,730
SecurityScorecard experts report that a large-scale botnet of more than 130,000 compromised devices is conducting password spraying attacks on Microsoft 365 accounts worldwide. The attack targets the legacy Basic Authentication (Basic Auth) authentication mechanism, which allows attackers to bypass multi-factor authentication (MFA).
The cybercriminals use credentials stolen using a keylogger. The attack is carried out through non-interactive login attempts using Basic Auth, which allows the attackers to evade the security system.
Experts warn that organizations relying solely on monitoring interactive logins remain vulnerable. Non-interactive logins, often used for service connections and legacy protocols (e.g. POP, IMAP, SMTP), in most cases do not require confirmation via MFA. Despite Microsoft's gradual phasing out of Basic Auth, it is still enabled in some enterprise environments, making it an attractive target for attacks.
Basic Auth is used to brute-force accounts with commonly used (or leaked) passwords. If the password is successfully brute-forced, MFA is not activated, allowing hackers to access the account without additional confirmations. The same mechanism allows bypassing Conditional Access Policies, making the attack virtually undetectable.
Once credentials are compromised, attackers can gain access to legacy services that do not support MFA, or use the data for further phishing attacks to completely take over accounts. Signs of attacks can be found in Entra ID logs. Signs include an increase in non-interactive login attempts, multiple failed authorization attempts from different IP addresses, and the presence of the "fasthttp" agent in the logs.
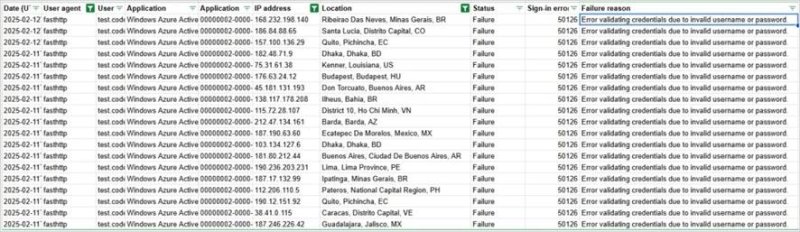
[td]Failed Login Attempts (SecurityScorecard)[/td]Researchers speculate that the botnet may be linked to groups from China, although there is no exact data yet. The attack scales by distributing login attempts across a huge number of IP addresses, making it difficult to detect and block the botnet.
The botnet is controlled via 6 C2 servers located in the infrastructure of the American provider Shark Tech, and the traffic passes through the hosting of UCLOUD HK (Hong Kong) and CDS Global Cloud (China). The C2 servers are based on Apache Zookeeper and Kafka, and the system time zone is set to Asia/Shanghai. Uptime logs show that the botnet has been active since December 2024.
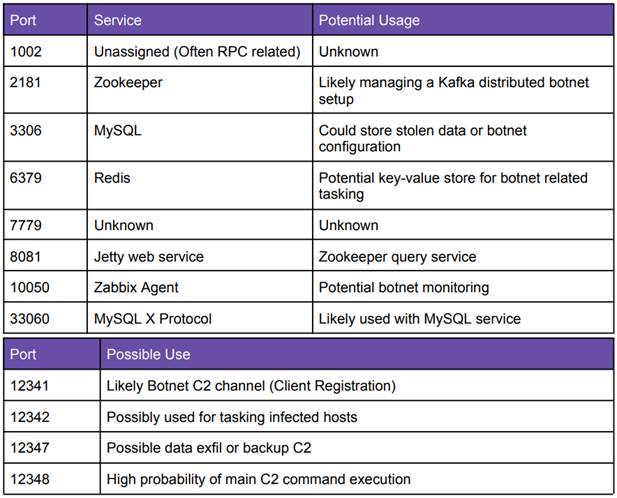
[td]Ports used for botnet control (SecurityScorecard)[/td]Experts recommend that organizations immediately disable Basic Authentication in Microsoft 365, block the IP addresses reported in the report, and enable conditional access policies to limit sign-in attempts. They should also enable MFA for all accounts and monitor suspicious sign-in attempts via Entra ID.
The cybercriminals use credentials stolen using a keylogger. The attack is carried out through non-interactive login attempts using Basic Auth, which allows the attackers to evade the security system.
Experts warn that organizations relying solely on monitoring interactive logins remain vulnerable. Non-interactive logins, often used for service connections and legacy protocols (e.g. POP, IMAP, SMTP), in most cases do not require confirmation via MFA. Despite Microsoft's gradual phasing out of Basic Auth, it is still enabled in some enterprise environments, making it an attractive target for attacks.
Basic Auth is used to brute-force accounts with commonly used (or leaked) passwords. If the password is successfully brute-forced, MFA is not activated, allowing hackers to access the account without additional confirmations. The same mechanism allows bypassing Conditional Access Policies, making the attack virtually undetectable.
Once credentials are compromised, attackers can gain access to legacy services that do not support MFA, or use the data for further phishing attacks to completely take over accounts. Signs of attacks can be found in Entra ID logs. Signs include an increase in non-interactive login attempts, multiple failed authorization attempts from different IP addresses, and the presence of the "fasthttp" agent in the logs.

The botnet is controlled via 6 C2 servers located in the infrastructure of the American provider Shark Tech, and the traffic passes through the hosting of UCLOUD HK (Hong Kong) and CDS Global Cloud (China). The C2 servers are based on Apache Zookeeper and Kafka, and the system time zone is set to Asia/Shanghai. Uptime logs show that the botnet has been active since December 2024.

