- 883
- 242
The Redis security team has released patches for a critical vulnerability that allows attackers to remotely execute arbitrary code. The issue has been present in the code for approximately 13 years.
The vulnerability, identified as CVE-2025-49844 (CVSS score 10 out of 10), is a use-after-free bug that can be exploited by authenticated attackers using a specially crafted Lua script (enabled by default).
Successful exploitation of this bug allows attackers to escape the Lua sandbox, trigger a use-after-free vulnerability, install a reverse shell for persistent access, and achieve remote code execution on the target Redis host.
After compromising the host, attackers can steal credentials, deploy malware, extract sensitive data from Redis, perform lateral movement to extend the attack to other systems on the victim's network, or use the stolen information to access cloud services.
[td]"This gives an attacker full access to the host system, allowing them to extract, destroy, or encrypt sensitive data, seize resources, and facilitate lateral movement in cloud environments," explain researchers at Wiz, who demonstrated the vulnerability at the Pwn2Own Berlin competition in May 2025, dubbing it RediShell.[/td]
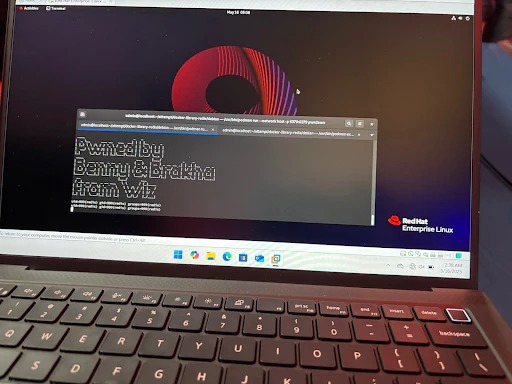
Although attackers need authenticated access to a Redis instance to successfully exploit the bug, Wiz analysts discovered approximately 330,000 accessible Redis instances online, at least 60,000 of which do not require authentication.
Redis and Wiz researchers urged administrators to immediately install the patches released last week, prioritizing internet-accessible instances.
To further protect Redis from remote attacks, administrators are advised to enable authentication, disable Lua scripting and other unnecessary features, run Redis as a non-root user, enable Redis logging and monitoring, restrict access to authorized networks, and implement network-level access control using firewalls and VPCs.
[td]"RediShell (CVE-2025-49844) is a critical vulnerability affecting all versions of Redis, as the root cause of the issue lies in the underlying Lua interpreter. With hundreds of thousands of internet-accessible instances worldwide, this vulnerability poses a serious threat to organizations across all industries," warn Wiz in their report .[/td]
The vulnerability, identified as CVE-2025-49844 (CVSS score 10 out of 10), is a use-after-free bug that can be exploited by authenticated attackers using a specially crafted Lua script (enabled by default).
Successful exploitation of this bug allows attackers to escape the Lua sandbox, trigger a use-after-free vulnerability, install a reverse shell for persistent access, and achieve remote code execution on the target Redis host.
After compromising the host, attackers can steal credentials, deploy malware, extract sensitive data from Redis, perform lateral movement to extend the attack to other systems on the victim's network, or use the stolen information to access cloud services.

Although attackers need authenticated access to a Redis instance to successfully exploit the bug, Wiz analysts discovered approximately 330,000 accessible Redis instances online, at least 60,000 of which do not require authentication.
Redis and Wiz researchers urged administrators to immediately install the patches released last week, prioritizing internet-accessible instances.
To further protect Redis from remote attacks, administrators are advised to enable authentication, disable Lua scripting and other unnecessary features, run Redis as a non-root user, enable Redis logging and monitoring, restrict access to authorized networks, and implement network-level access control using firewalls and VPCs.
