- 23
- 1
- 3
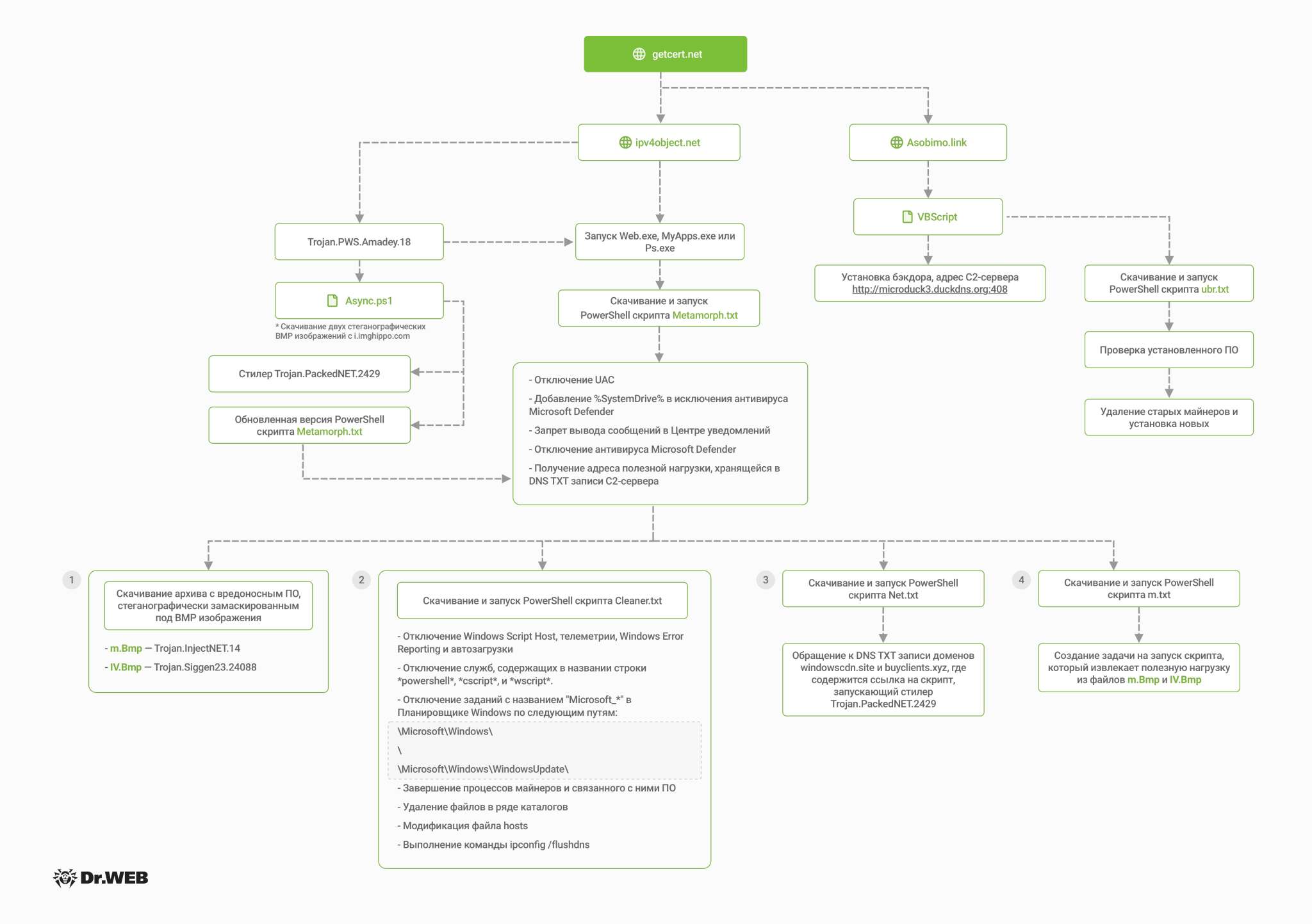
Doctor Web specialists have discovered malware samples that, upon closer inspection, turned out to be components of an active campaign to mine the Monero cryptocurrency. Two malicious chains are built on running scripts that extract malicious payloads from BMP image files.
According to the researchers, this campaign has been active since 2022, as evidenced by the Services.exe executable file, which is a .NET application that runs a VBscript script. This script implements backdoor functions by contacting the attackers' server and executing scripts and files sent in response. Thus, a malicious file ubr.txt is downloaded to the victim's computer, which is a script for the PowerShell interpreter, the extension of which was changed from ps1 to txt.
The script checks for miners that may have already been installed on the compromised machine and replaces them with the versions needed by the attackers. The files installed by the script are the SilentCryptoMiner miner and its settings.
It is noted that within the framework of this campaign, the miner files are disguised as various software, for example, for video calls in Zoom (ZoomE.exe and ZoomX.exe) or Windows services (Service32.exe and Service64.exe).
In addition, the miner accesses the getcert[.]net domain, where the m.txt file with cryptocurrency mining settings is located. This resource was also used in other attack chains.
Experts write that now the attackers have modified the attack methodology, making it more interesting, and have begun to use steganography.
Thus, the second, newer attack chain is implemented using the Amadey Trojan, which runs the Async.ps1 PowerShell script, which downloads BMP images from the legitimate image hosting imghippo.com. Using steganography, two executable files are extracted from these images: the Trojan.PackedNET.2429 stealer and the payload, which:
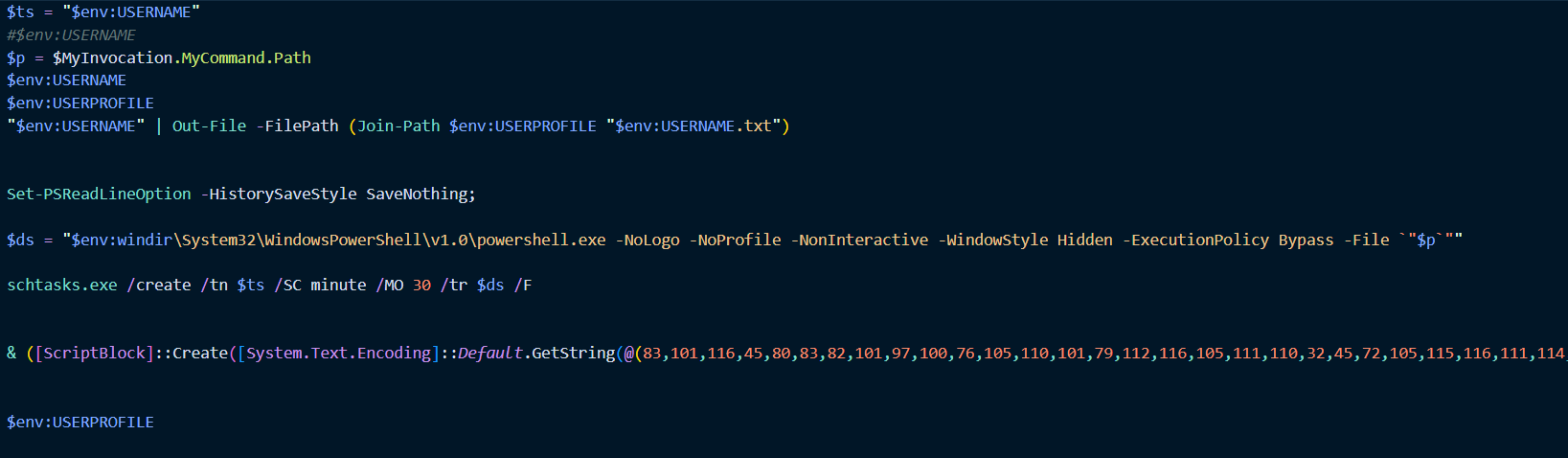
[td]Contents of Async1.ps[/td]During the execution of this task, the attackers' domains are accessed, the DNS TXT record of which contains the storage address of the subsequent payload. After downloading them, the archive with BMP images is unpacked and the following files are launched:
[td]Attack scheme[/td]One of the wallets specified in the miner settings was created back in May 2022, and as of today, 340 XMR have been transferred to it, meaning the scammers' profit could be between 6 and 7.5 million rubles.
Based on the hashrate fluctuations (which indicate regular computer switching on and off), the researchers believe that this mining campaign is mainly involving ordinary users located in the same group of time zones. The average hashrate is 3.3 million hashes per second, which allows compromised machines to bring the attackers 1 XMR every 40 hours.
According to the researchers, this campaign has been active since 2022, as evidenced by the Services.exe executable file, which is a .NET application that runs a VBscript script. This script implements backdoor functions by contacting the attackers' server and executing scripts and files sent in response. Thus, a malicious file ubr.txt is downloaded to the victim's computer, which is a script for the PowerShell interpreter, the extension of which was changed from ps1 to txt.
The script checks for miners that may have already been installed on the compromised machine and replaces them with the versions needed by the attackers. The files installed by the script are the SilentCryptoMiner miner and its settings.
It is noted that within the framework of this campaign, the miner files are disguised as various software, for example, for video calls in Zoom (ZoomE.exe and ZoomX.exe) or Windows services (Service32.exe and Service64.exe).
In addition, the miner accesses the getcert[.]net domain, where the m.txt file with cryptocurrency mining settings is located. This resource was also used in other attack chains.
Experts write that now the attackers have modified the attack methodology, making it more interesting, and have begun to use steganography.
Thus, the second, newer attack chain is implemented using the Amadey Trojan, which runs the Async.ps1 PowerShell script, which downloads BMP images from the legitimate image hosting imghippo.com. Using steganography, two executable files are extracted from these images: the Trojan.PackedNET.2429 stealer and the payload, which:
- Disables the UAC elevation prompt for administrators;
- makes many exceptions to Windows Defender;
- disables notifications in Windows;
- creates a new task in the path \Microsoft\Windows\WindowsBackup\ with the name User.

- txt - PowerShell script that removes any other miners;
- txt — a PowerShell script that extracts the payload from the m.bmp and IV.bmp images (the payload inside the images is the SilentCryptoMiner miner and the injector that launches it);
- txt is a script that reads the DNS TXT record for the windowscdn[.]site and buyclients[.]xyz domains. This record contains a link to the payload, which leads to raw.githack[.]com.

Based on the hashrate fluctuations (which indicate regular computer switching on and off), the researchers believe that this mining campaign is mainly involving ordinary users located in the same group of time zones. The average hashrate is 3.3 million hashes per second, which allows compromised machines to bring the attackers 1 XMR every 40 hours.
