- 893
- 246
LayerX researchers discovered 30 malicious extensions disguised as AI assistants in the Chrome Web Store. At the time of discovery, they had been installed by more than 300,000 users. The extensions steal passwords, email content, and browser data. Some of the malware is still available in the official Chrome Store.
The researchers dubbed this malicious campaign AiFrame. According to them, all 30 extensions operate as part of a single operation, communicating with infrastructure under the domain tapnetic[.]pro.
The most popular extension in this campaign was Gemini AI Sidebar (fppbiomdkfbhgjjdmojlogeceejinadg), with over 80,000 installations. Google has since removed it from the store. However, other extensions with thousands of users are still available for download. According to Bleeping Computer , the Chrome Web Store still contains:
In the background, the extensions extract the content of pages visited by the user, including authentication pages. This is done using the Mozilla Readability library.
Furthermore, according to researchers, 15 of the 30 extensions specifically target Gmail and use a separate content script that runs on mail.google.com and injects UI elements. This script reads the visible content of emails from the DOM and continuously extracts the text of the email thread via .textContent. Experts emphasize that even draft emails can be intercepted in this manner.
[td]"When Gmail features like AI replies or summaries are activated, the extracted email content is passed to the extension's logic and sent to third-party servers controlled by its operators," the experts write. "As a result, the message text and contextual data leave the device and escape Gmail's protections, reaching remote servers."[/td]In addition to the above, these extensions can remotely activate voice recognition and transcript generation using the Web Speech API, returning the results to the attackers. Depending on the permissions granted, the malware can even intercept conversations from the victim's surroundings.
Anyone who has used any of these malicious extensions is advised to immediately remove them and then change the passwords for all accounts. A full list of indicators of compromise and dangerous extensions is available in the LayerX report .

The researchers dubbed this malicious campaign AiFrame. According to them, all 30 extensions operate as part of a single operation, communicating with infrastructure under the domain tapnetic[.]pro.
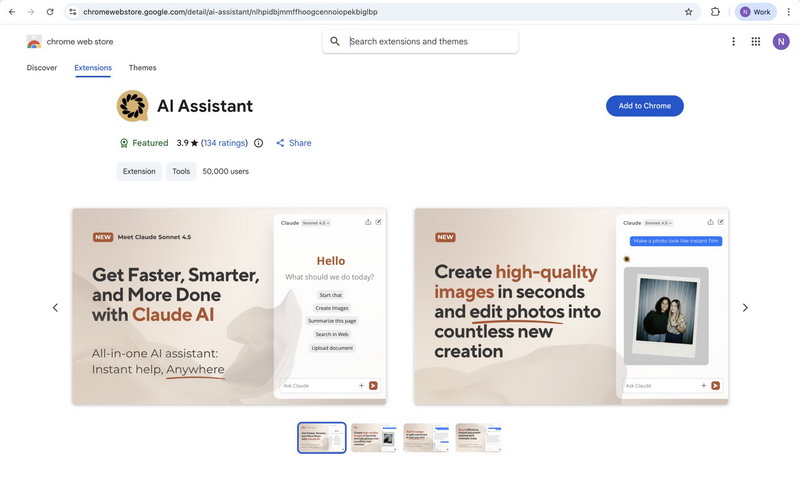
The most popular extension in this campaign was Gemini AI Sidebar (fppbiomdkfbhgjjdmojlogeceejinadg), with over 80,000 installations. Google has since removed it from the store. However, other extensions with thousands of users are still available for download. According to Bleeping Computer , the Chrome Web Store still contains:
- AI Sidebar (gghdfkafnhfpaooiolhncejnlgglhkhe) — 70,000 installations;
- AI Assistant (nlhpidbjmmffhoogcennoiopekbiglbp) — 60,000 installations;
- ChatGPT Translate (acaeafediijmccnjlokgcdiojiljfpbe) — 30,000 installations;
- AI GPT (kblengdlefjpjkekanpoidgoghdngdgl) — 20,000 installations;
- ChatGPT (llojfncgbabajmdglnkbhmiebiinohek) — 20,000 installations;
- AI Sidebar (djhjckkfgancelbmgcamjimgphaphjdl) — 10,000 installations;
- Google Gemini (fdlagfnfaheppaigholhoojabfaapnhb) — 10,000 installations.
In the background, the extensions extract the content of pages visited by the user, including authentication pages. This is done using the Mozilla Readability library.
Furthermore, according to researchers, 15 of the 30 extensions specifically target Gmail and use a separate content script that runs on mail.google.com and injects UI elements. This script reads the visible content of emails from the DOM and continuously extracts the text of the email thread via .textContent. Experts emphasize that even draft emails can be intercepted in this manner.
Anyone who has used any of these malicious extensions is advised to immediately remove them and then change the passwords for all accounts. A full list of indicators of compromise and dangerous extensions is available in the LayerX report .
